Akira Ransomware Targets Cisco VPNs
Akira ransomware, debuting in March 2023, targets Cisco VPNs with a unique approach, drawing inspiration from the 1988 anime film 'Akira'. This cyber threat emphasizes the importance of multi-factor authentication and robust cybersecurity measures.

Introduction to Akira Ransomware
In the ever-evolving landscape of cybersecurity threats, a relatively new player called Akira ransomware made its debut in March 2023. While its name might ring a bell due to a 2017 ransomware strain with the same moniker, this new Akira ransomware takes a different approach. Unlike its predecessor, which shared no code similarities, this fresh threat has an interesting twist - it draws inspiration from the 1980s. Specifically, it pays homage to the iconic cyberpunk aesthetic of the 1988 anime film "Akira." But don't let its nostalgic design fool you; this ransomware means business. It incorporates a retro-inspired victim site design that mirrors the green-screen consoles of the '80s. Even more intriguing, this site allows victims to send commands, going beyond the typical information display.
Akira, the ransomware group responsible for these attacks, operates with an unconventional payment approach. They place a daunting decision in the hands of their victims: determining the ransom amount they are willing to pay. This sum can fluctuate significantly, ranging from $200,000 USD to upwards of $4 million USD, based on insights gathered from Arctic Wolf® Incident Response. However, there's a significant twist to this situation: those who refuse to meet the ransom demand face a distressing predicament. Akira's policy is to expose the victim's identity and data on their leak site, a tactic that undoubtedly exerts tremendous pressure on organizations to comply with their demands.
Since its inception, Akira has set its sights on and compromised no fewer than 63 organizations. Notably, approximately 80% of these victims fall into the category of small to medium-sized businesses (SMBs), indicating the group's proclivity for targeting entities of this scale. An intriguing aspect to note is that some of the initially listed victims on the leak site have subsequently been removed, leaving room for speculation regarding the motives behind such actions. Furthermore, the impact of these attacks has rippled across various industries. Prominent sectors include manufacturing, education and non-profit organizations, finance and insurance, as well as legal and government entities.
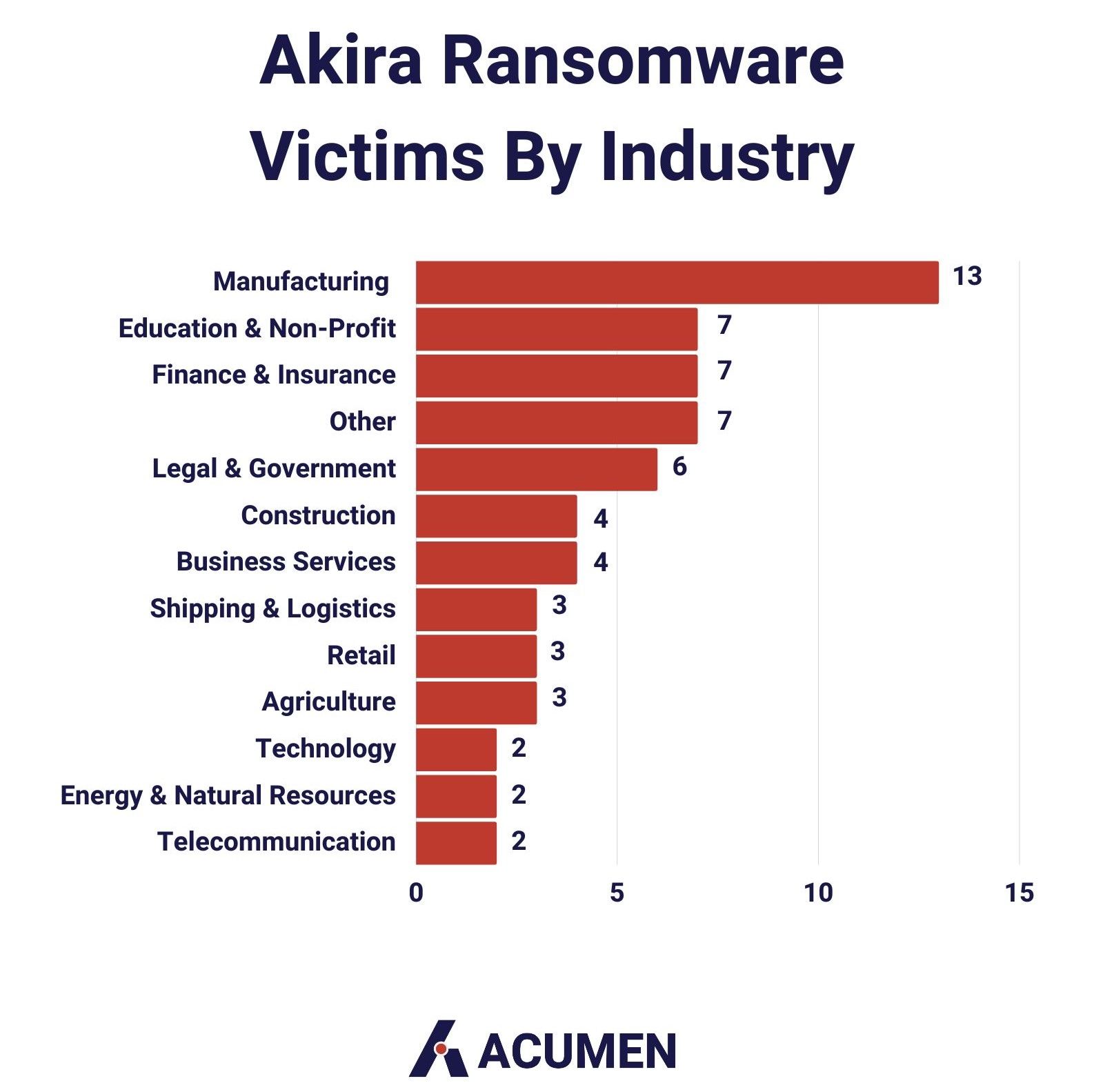
While Akira's visual presentation might harken back to the past, its impact is very much felt in the present. It has already caused disruptions across the globe, affecting organizations of all sizes. While its victim count may currently be modest compared to some more infamous ransomware strains, we should bear in mind that these threats tend to start small and can swiftly escalate.
Akira's Preferred Target: Cisco VPNs
One distinguishing characteristic of Akira ransomware is its preference for Cisco VPNs as its preferred point of entry. Attackers behind Akira typically exploit compromised credentials or vulnerabilities within VPN software. Their primary focus seems to be on systems lacking multi-factor authentication (MFA). This has been confirmed by research conducted by Rapid7, which indicates that these attacks have been ongoing since March 2023.
The modus operandi of these attackers involves brute-force attempts to crack login credentials. It's crucial to note that, as of now, there have been no reported cases of them successfully bypassing properly configured MFA systems to breach Cisco VPNs. This underscores the significance of implementing robust MFA as part of your security strategy.
Rapid7's research has also revealed that at least 11 customers have fallen victim to attacks related to Cisco ASA (Adaptive Security Appliance) between March 30 and August 24. These breaches have been traced back to compromised SSL VPNs. Attackers often target common usernames, highlighting the critical need for strong, unique credentials and the diligent implementation of MFA.
In a blog article by Cisco's own Omar Santos, the importance of MFA in mitigating Akira attacks on Cisco VPNs is underscored. Santos recommends implementing MFA as a foundational defense strategy to fend off unauthorized access attempts and potential ransomware infiltration. Collaboration with security experts from Rapid7 is also mentioned. Additional recommendations encompass keeping software updated, patching vulnerabilities, adhering to cybersecurity best practices, practicing network segmentation, following the Principle of Least Privilege, data encryption, and developing comprehensive continuity and incident response plans.
Gaining Insights from Sophos
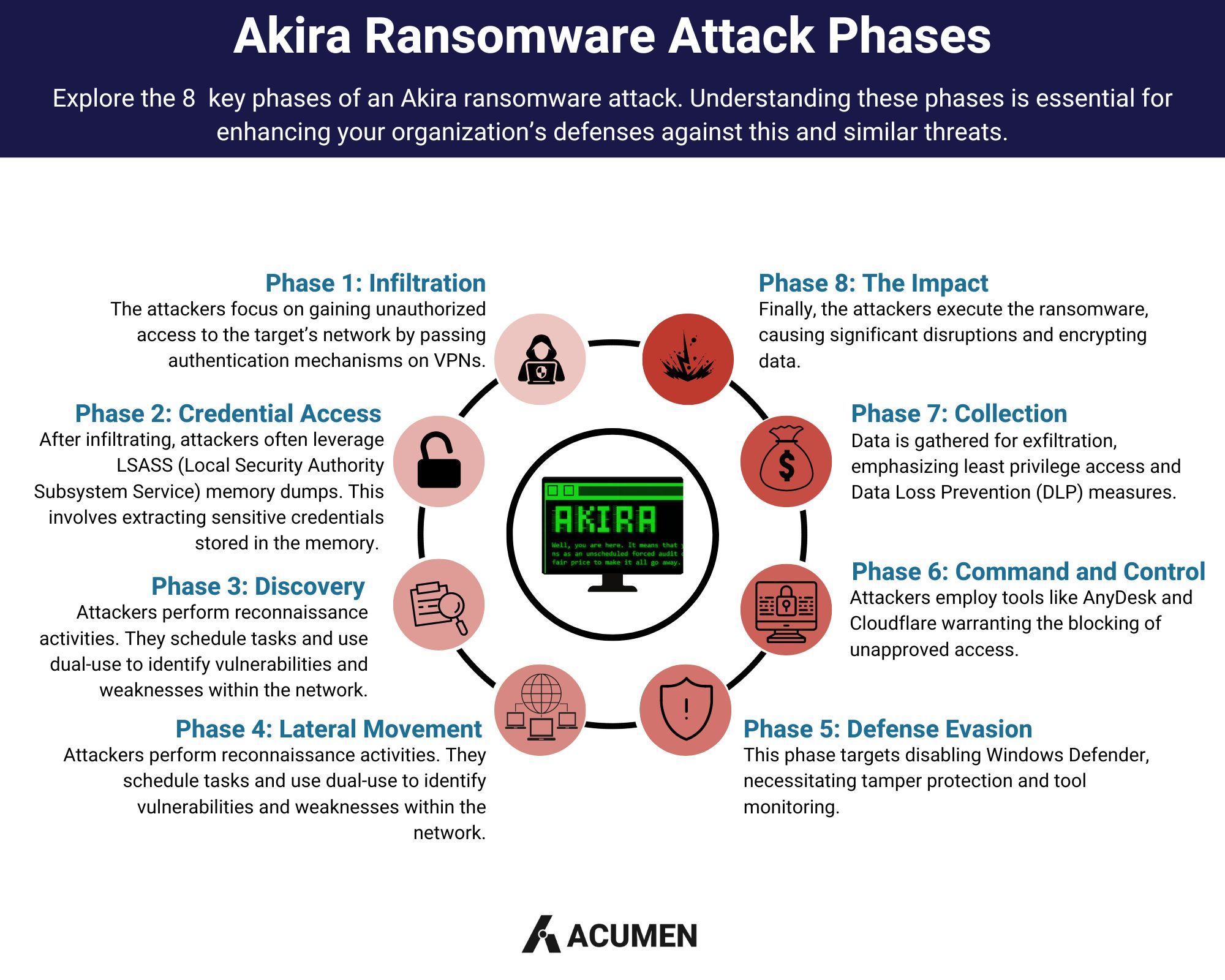
A deeper understanding of Akira ransomware and the tactics, techniques, and procedures (TTPs) employed by the threat actors behind it can be gleaned from Sophos' extensive examination of Akira attacks. While these findings may not directly relate to Akira's recent assault on Cisco VPNs, they offer invaluable insights into the group's operational strategies. Armed with this knowledge, organizations can bolster their defenses, even against emerging threats.
Akira's attack methodology spans various phases:
Crafting a Comprehensive Defense Strategy
In the face of the Akira ransomware threat, organizations must adopt a multi-pronged defense strategy. The foremost element is the implementation of Multi-Factor Authentication (MFA). Given Akira's specific targeting of Cisco VPNs lacking MFA, its adoption is critical. MFA shines by demanding multiple forms of user verification, significantly reducing the risk of unauthorized access, even in cases of compromised credentials.
Concurrently, organizations should adhere to fundamental security practices such as regular software patching, comprehensive employee training, and robust logging to fortify their defenses against this specific threat.
Early Detection and Effective Recovery
Swiftly detecting an Akira attack is paramount to minimizing the damage. Indications of an Akira breach include unexpected file encryption, inaccessible data, ransom notes, irregular network traffic, and unauthorized access attempts. Organizations should actively monitor their systems for unusual activities, analyze logs for signs of compromise, and remain vigilant.
To enhance their ability to detect potential exploitation, organizations should consider continuous network monitoring, thorough log analysis, intrusion detection and prevention systems, and the utilization of Security Information and Event Management (SIEM) solutions. Additionally, endpoint security tools provide real-time threat detection to bolster overall security posture.

A Structured Approach to Recovery
Recovering from an Akira ransomware attack demands a structured approach. Begin with a comprehensive assessment and system isolation to contain the breach. Next, focus on malware removal, either through reputable antivirus software or the assistance of cybersecurity experts. Data restoration should involve clean and secure backups that remain unaffected by the ransomware. Identifying and patching vulnerabilities exploited by attackers is paramount. Continuous monitoring of restored systems is necessary to detect any signs of reinfection, and thorough security testing ensures vulnerabilities are addressed, guaranteeing a secure environment.

Proactive Detection and Alerting
Proactive detection and alerts are key to combating Akira and similar threats effectively. Strategies such as configuring firewalls to block malicious traffic, enabling comprehensive logging with centralized log management, and employing intrusion detection and prevention systems provide real-time alerts.
Security Information and Event Management (SIEM) platforms can aggregate and analyze security data from various sources, aiding in threat detection. Network segmentation and strict access controls limit an attacker's lateral movement. Regular patching, employee training, and phishing awareness are fundamental in building a robust security posture.
Best Practices for Configuration and Setup
Lastly, configuring and setting up defenses against Akira ransomware involves adopting best practices. These encompass developing a robust incident response plan, collaborating with threat intelligence providers, and deploying advanced endpoint security tools. Continuous network monitoring and regular review of security logs are essential. Network segmentation, Multi-Factor Authentication (MFA), and encryption add layers of protection. Detailed incident logging, secure data backups, and effective security policies and procedures are vital. Managing third-party risks, keeping stakeholders informed, and fostering collaboration between IT, security teams, and management complete the comprehensive strategy against Akira and similar threats.

By following these guidelines and implementing a comprehensive defense strategy, organizations can better shield themselves from the Akira ransomware threat and stay ahead of evolving cyber threats in the ever-changing cybersecurity landscape.
References:
- Arghire, I. (2023, July 26). Dozens of Organizations Targeted by Akira Ransomware. Security Week. https://www.securityweek.com/dozens-of-organizations-targeted-by-akira-ransomware/
- Campbell, S., Suthar, A., Belfiore, C., & Arctic Wolf Labs Team. (2023, July 26). Conti and Akira: Chained Together. Arctic Wolf. https://arcticwolf.com/resources/blog/conti-and-akira-chained-together/
- Delta-Sierra_426. (2023, August 22). Akira Ransomware Targets Cisco VPNs. Spiceworks. https://community.spiceworks.com/topic/2492752-akira-ransomware-targets-cisco-vpns?source=headlined
- Gatlan, S. (2023, August 30). Hacking campaign bruteforces Cisco VPNs to breach networks. Bleeping Computer. https://www.bleepingcomputer.com/news/security/hacking-campaign-bruteforces-cisco-vpns-to-breach-networks/
- Jaramillo, P. (2023, May 09). Akira Ransomware is “bringin’ 1988 back”. Sophos. https://news.sophos.com/en-us/2023/05/09/akira-ransomware-is-bringin-88-back/#:~:text=A%20new%20recently%20observed%20ransomware,film%20of%20the%20same%20name
- Kennedy, C. (2023, August 23). PSA—Akira Ransomware Targeting Cisco VPNs. Aragon Research. https://aragonresearch.com/psa-akira-ransomware-targeting-cisco-vpns/
- NJCCIC. (2023, August 24). Akira Ransomware Targeting New Jersey Organization. Njccic. https://www.cyber.nj.gov/garden_state_cyber_threat_highlight/akira-ransomware-targeting-new-jersey-organization
- Santos, O. (2023, August 24). Akira Ransomware Targeting VPNs without Multi-Factor Authentication. Cisco Blogs. https://blogs.cisco.com/security/akira-ransomware-targeting-vpns-without-multi-factor-authentication
- Toulas, B. (2023, August 22). Akira ransomware targets Cisco VPNs to breach organizations. BleepingComputer. https://www.bleepingcomputer.com/news/security/akira-ransomware-targets-cisco-vpns-to-breach-organizations/






