Behind the Bait: A Guide on Phishing and How to Stay Safe
Phishing continues to be a developing threat actor tactic that spawns some of the most creative cyber-attacks.

Phishing poses a significant threat in the digital landscape, exploiting typical human behaviors as the primary point of entry into secure systems. Phishing is a cyber-attack tactic where malicious actors use fraudulent emails, messages, or websites to deceive individuals or organizations into revealing sensitive information. By impersonating legitimate entities, they aim to steal personal credentials, financial data, or intellectual property through social engineering tactics, compromising security. Phishing has accounted for an alarming portion of the world's cyber-attacks. The IBM x-Force Threat Intelligence Index highlights that phishing was responsible for 30% of initial breach methods in all cyberattacks during 2023. In addition, Greathorn reports that 57% of organizations experience phishing attempts weekly or daily, emphasizing the persistent threat these attacks pose. According to IBM, the average cost of a phishing attack in 2023 was $4.76 million, factoring in legal fines, system reparations, loss of business, and operational downtime, making it one of the costliest types of attacks.
Phishing continues to be a developing threat actor tactic that spawns some of the most creative cyber-attacks. For instance, in February of 2024, a Hong Kong finance employee fell victim to a sophisticated scheme where they were tricked into transferring $25.6 million to a fraudulent account. Using deepfake technology, the perpetrators convincingly impersonated company executives during a virtual meeting. Attacks like these are why organizations around the world need to take phishing as a serious evolving threat. Understanding the intricacies of phishing attacks is crucial for implementing robust cybersecurity measures. This entails learning to recognize and defend against such threats and leveraging available tools to enhance phishing.
Understanding Phishing
Phishing is an attack that started thanks to the rapid adoption of Electronic Mailing Services in the early 2000s; this served as the ideal environment to refine and improve attacks with frequency and effectiveness. Eventually, the FBI took notice of the rise of the Business Email Compromise (BEC). BEC is where attackers impersonate legitimate entities to trick individuals into transferring funds or sensitive information via email or other corporate messaging systems. This would later evolve into phishing. Eventually, attackers began developing tools in the early 2010s that would coalesce around specific technologies, such as Microsoft Exchange, as it was the fastest-growing email software for the foreseeable future. Fast forward to 2023, 83% of large companies were using Microsoft Exchange as their email service. As a result, 92% of those organizations have fallen victim to a phishing attack. A phishing attack is akin to a game of deception, where malicious actors use disguises to falsely gain the trust of their victims. These deceptions are explained more clearly in the Diagram below.
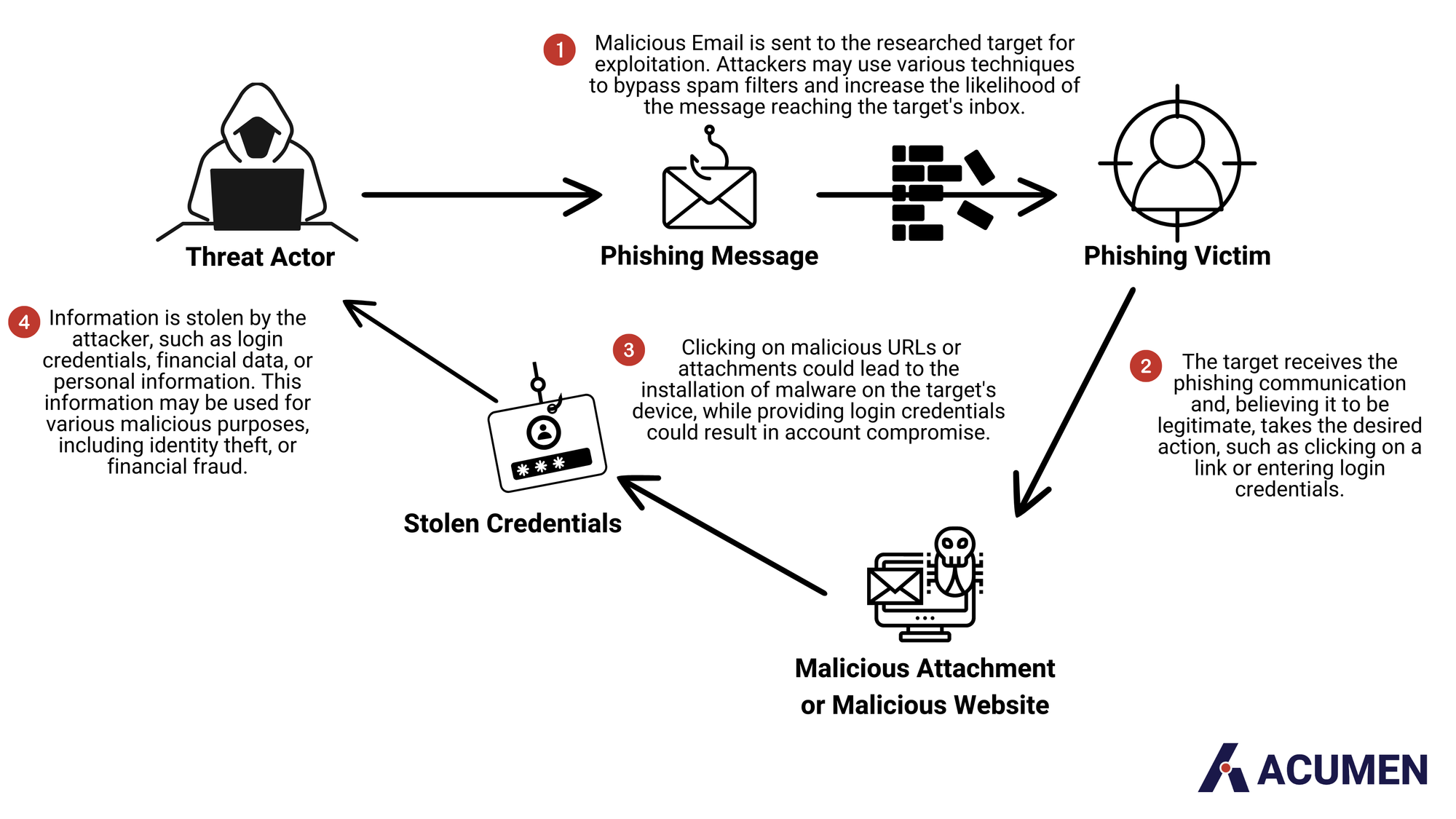
Furthermore, this is not the only type of phishing attack that exists today. Below are some other common phishing attacks:
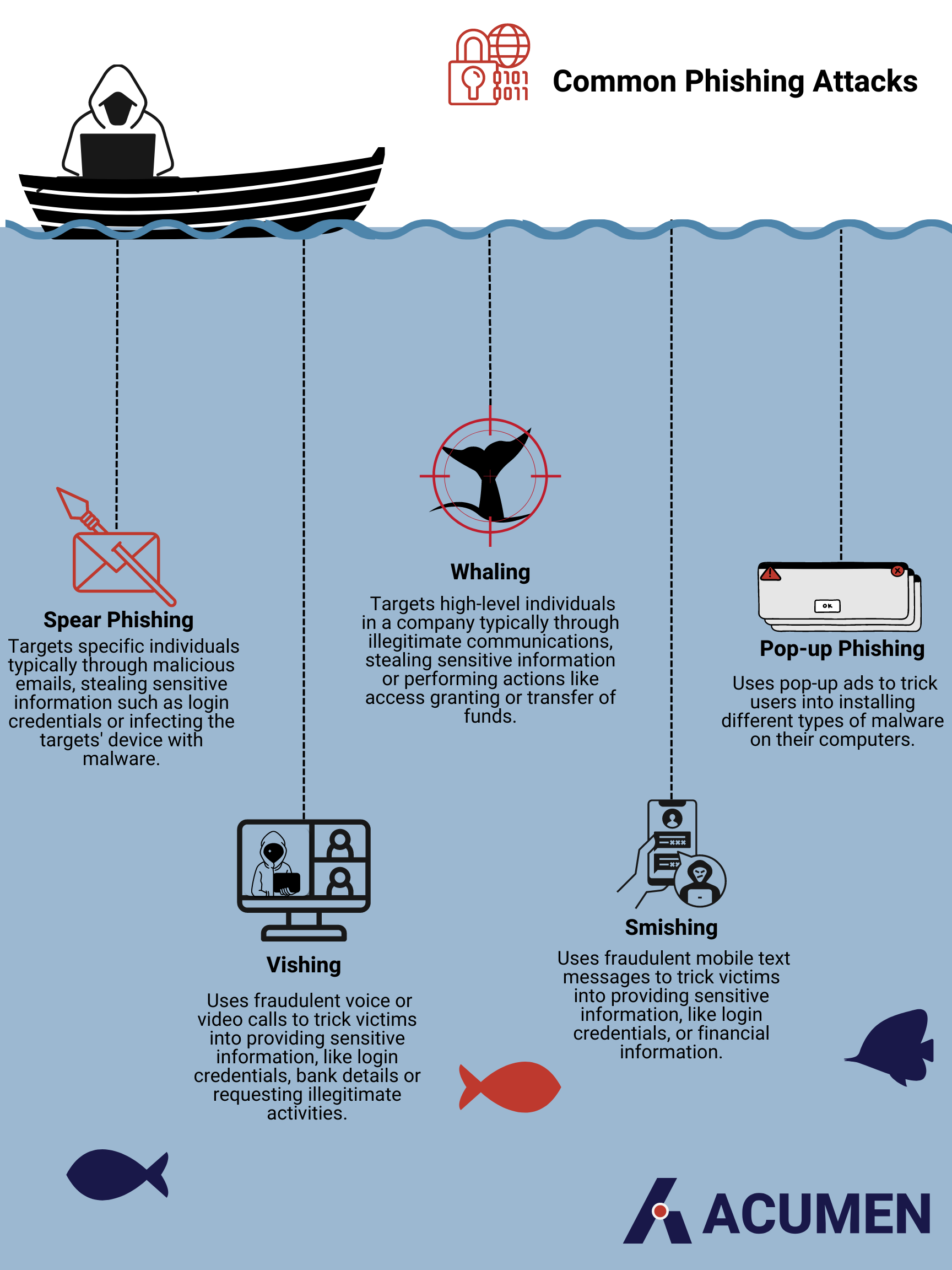
Detecting a Phish
Detecting a phishing attack continues to be an increasingly hard task due to threat actors constantly evolving their methods of attack and exploitation of human nature. Despite the advancement of cyber security tools and training, phishing remains one of the leading causes of devastating cyberattacks around the world. However, certain elements of these attacks exhibit patterns that, if recognized, can prevent possible compromise and successful infiltration.
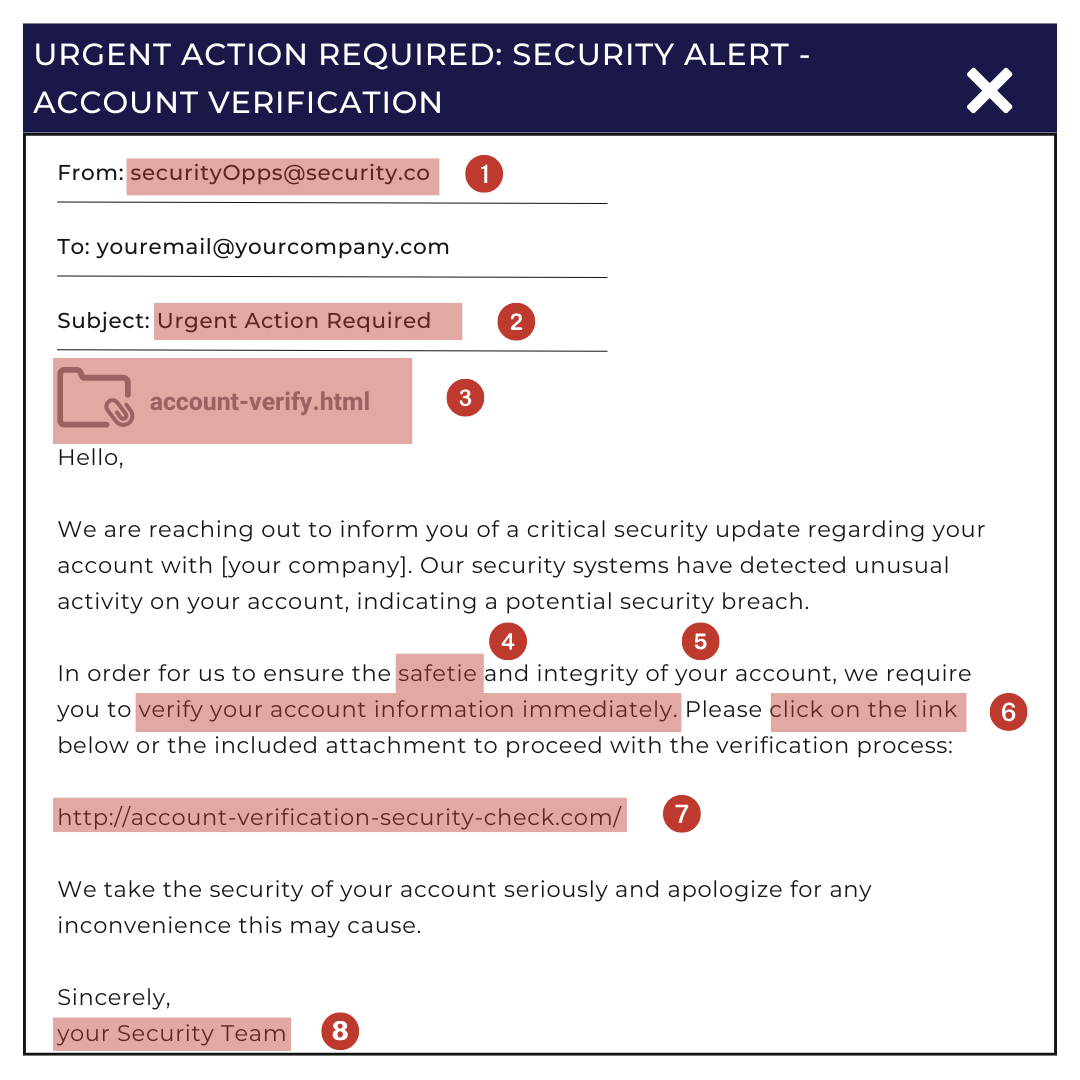
Phishing Analysis Checklist:
Areas of Concern-
Sender Address:
Analyze the message's sender; is the address suspicious or spoofed? If the address is similar or identical to your organization's typical email address, investigate its domain extension (.net, .com, .ca, .gov) to see if it is logical for your organization to have an address like this.
-
Subject Line Contents:
Check for generic or unusual subject lines. Any subject line that is offering goods or prizes is under high suspicion. In addition, any messages that call for immediate action or contact are usually suspected of being malicious in nature.
-
Attachments:
Attachments are highly prone to containing malware, ransomware, and other dangerous scripts. Do not open them unless you are expecting an attachment from the sender. Files containing malicious software include .pdf, .xlsx, .docx, .iso, .exe, .txt, and .zip.
-
Spelling and Grammar:
Professional emails within an organization are usually checked for spelling and grammar. Always check for outstanding errors that are not common in a professional email. However, the language, grammar, and tone of emails are increasingly becoming grey areas with the prevalent use of AI to draft such emails.
-
Urgent Call to Respond or Comply:
Contents of an email that encourage you to perform an action or navigate to a certain URL outside your email should be considered suspicious. An organization usually has an outlined procedure for you to handle various processes; always consult with that or your colleagues to verify if the action required is a normal one.
-
Pressure to Perform Action:
Performing any action, such as clicking a link or attachment, should not be done unless it is a common and known process. Always verify with your IT or security team if these messages are normal.
-
Suspicious Links:
Analyze the links to make sure that they do not contain any strange characters or end in any possibly strange domain extensions such as .country, .download, .xin, .gdn, .loan or .win.
-
Non-Identifiable Company Signature:
Company signatures are a unique way of identifying members of your organization; they are very hard to recreate due to usually not being available to the public. Always check if the signature is formatted and ends appropriately or if the message has a signature at all.
Phishing continues to be a progressive attack because new technologies are becoming integrated into it. AI tools currently allow users to easily amalgamate research from target organizations within seconds and create more accurate and inconspicuous-appearing attacks. In addition, they can recreate typing and speaking patterns via publicly available information to trick users into a false sense of security.
Defending against phishing attacks requires vigilance, preparedness, and a degree of knowledge necessary to allow for skepticism when receiving a potential phish. We advise the following security measures to improve security posture against phishing.
Employee training and awareness: Educating all organization members on the dangers of phishing is critical to guarantee safety. Employees, including executives, should participate in training, as they can also fall victim to attacks like these (for example, Spear Phishing and Whaling). According to IBM, implementing a high level of training reduces the cost of the average data breach by approximately 33.9% ($1.5 million USD), making it the second highest cost mitigator behind implementing a DevSecOps Approach to your organization.
Effective training is recommended to be concise, engaging, and straightforward to transmit the clear and important concepts of phishing. It is recommended to teach employees to recognize phishing emails and suspicious URLs, while encouraging prompt reporting of any concerning messages or websites. Consistent delivery is also advised to keep the threat of these attacks fresh in the minds of organization members. Finally, integrating real-life elements such as phishing attack simulations or providing printed checklists or posters of warning signs can enhance employee readiness and awareness beyond their workstations.
Implementing security controls such as filtering and sender authentication (MFA):
Implementing restrictions and security controls can direct messages from non-trusted senders to a separate folder like spam or junk. Additionally, filters can function as standalone appliances in conjunction with internal email serves, routing mail through anti-spam systems before even reaching the email server, for enhanced security. Web filters (proxies) can blacklist potentially harmful sites, preventing users from accessing them if they click a link.
Furthermore, technology such as multifactor authentication (MFA) is vital when handling sensitive information through corporate messaging systems. MFA adds an extra layer of security beyond passwords by requiring additional verification, such as a text message code or the use of third-party software like Microsoft Authenticator. Despite these measures bolstering security, they are not infallible and can still be bypassed by skilled attackers. Therefore, they should complement existing security protocols rather than serve as standalone solutions.
Monitor traffic at rest and in transit for external communications:
Monitoring traffic at rest and in transit is essential for surveillance work when attempting to restrict suspicious activity in a network. Traffic at rest pertains to data stored in repositories, databases, and archives, while in transit involves data moving between systems like emails or file transfers. Active monitoring of both traffic at rest and traffic in transit enables the timely detection and response to potential threats, including unauthorized access and data exfiltration. This proactive approach allows for swift action, such as identifying suspicious URLs or attachments in transit and uncovering unauthorized access incidents at rest. Such rapid response measures mitigate damage and protect sensitive data, ultimately bolstering network security. Monitoring traffic is crucial for maintaining the security of a network and responding effectively to cyber incidents in a timely manner. Organizations can proactively identify and mitigate threats, ultimately safeguarding sensitive data and minimizing the impact of cyberattacks.
Responding to a Phishing Attack:
You have received what appears to be a suspicious email that you do not usually receive. It is advised to approach it in the following way.

Anti-Phishing Technologies:
If a malicious email or website has been sent to an employee, giving the employee the resources and systems necessary to analyze, defend, and report attacks is important. These systems could be as simple as forwarding emails to a specific folder or more advanced methods, such as using built-in phishing cyber tools. It is important to remember that technology is one of your best allies when dealing with phishing attacks. Below are some tools that can be used to better equip yourself against these attacks:
Email Header Analyzers: Examine the metadata of email messages to identify sender information, email routing, and potential manipulation of the contents that could have been tampered with or spoofed. An example of tools like this could be the Google Messageheader, or the Azure Header Analyzer.
URL Analyzers: Inspect website URLs for malicious content or phishing attempts by analyzing their structure, redirects, and embedded scripts. Examples of tools include Web Check and VirusTotal, which can handle both URLs and files.
Domain Info Retriever: Focuses on extracting comprehensive domain-related information for analysis, including website structures, registration information, hosting providers, and DNS records, to help identify irregularities or hidden elements that may indicate security threats or vulnerabilities. Use tools such as DomainTools - Reverse IP Lookup.
Website Visualizers: Provide visual representations of website structures, code, and content to help identify anomalies, malware, or hidden elements that may indicate security threats or vulnerabilities. The most well-known tool for this is urlscan.io.
Sandboxing: The process of isolating and executing suspicious or untrusted files, programs, or processes within a controlled environment. This prevents potential harm to the host system and allows analysis of its behaviour. Sandboxes are a very common tool in security teams. Popular browser-based tools include Browserling and Joe Sandbox.
Logging: Gather and preserve digital artifacts such as files, logs, registry entries, and network traffic associated with security incidents or investigations for further analysis and forensic examination if an incident occurs. Popular tools include Logstash and Splunk.
Phishing Simulators: Simulate phishing attacks to test an organization's users' awareness and responsiveness to potential phishing threats. Examples of phishing simulators include KnowBe4 and Confense's PhishMe.
In conclusion, understanding phishing attacks is crucial for safeguarding your organization online. By understanding the fundamentals of phishing and identifying a phish before it is too late, you can prevent possible incidents and enhance your cybersecurity posture. Additionally, learning about tools available to system administrators can further your understanding of phishing threats. Equipping yourself with the knowledge and resources that contribute to a safer digital environment is key.
References
- Baker, E. (2024, January 23). Top 10 costs of phishing - Hoxhunt. www.hoxhunt.com.
- Chen, H., & Magramo, K. (2024, February 4). Finance worker pays out $25 million after video call with deepfake “chief financial officer.” CNN. https://www.cnn.com/2024/02/04/asia/deepfake-cfo-scam-hong-kong-intl-hnk/index.html
- IBM Corporation. (2024). X-Force Threat Intelligence Index 2024. In ibm.com. https://www.ibm.com/reports/threat-intelligence
- Moss, J. (2023, April 3). AI is Making Phishing Emails Much Harder to Spot | Genmar IT. Genmar. https://genmar.co.uk/blog/ai-is-making-phishing-emails-much-harder-to-spot/
- Özşahan, H. (2024, March 12). 50+ Phishing Attack Statistics for 2024 | Resmo. www.resmo.com.
- Ponemon institute. (2023). Cost of a Data Breach Report 2023. In ibm.com. Ponemon Institute LLC. https://www.ibm.com/reports/data-breach






