Cyber Security Awareness Month Series Part 2: How to Build an Effective Cyber Security Risk Management Program

In appreciation for Cyber Security Awareness Month during October, we are excited to provide a three-part article series on Cyber Security Risk Management for Critical Infrastructure Executives and Board Directors. This series will cover the following topics:
- The Increasingly Threatening Cyber Threat Landscape for Critical Infrastructure Operators
- Guidelines on How to Build an Effective Cyber Security Risk Management Programs
- Proven Techniques on How to Implement Effective Cyber Security Governance Practices for Your Program
Cyber Security is not an IT issue – it is a risk management and governance concern that executives and Boards must tightly oversee, manage, and support. This includes physical security due to the association of physical breaches of key facilities and assets. Cyber security management should not be a standalone initiative; rather, it must be integrated into your overall enterprise risk management program.
The first part in the series provided a high level of context on the cyber security threat landscape and key risks for critical infrastructure operators. This second part in the series provides you with practical guidance on how to build an effective cyber security risk management program. The series will culminate in October with an exciting article on the topic of governance in cyber security.
Enjoy the series, and we hope this will assist you in your cyber security risk management initiatives!
Key Cyber Risk Management Concepts
Contrary to popular belief, cyber security is not an IT concern, but rather a risk management and governance issue. Executives and Boards need to be actively engaged to oversee, manage, and support the entity’s cyber security program.
Physical security goes hand-in-hand with cyber security risk management due to the association of physical breaches of key facilities and assets. A best practice is to look at cyber security and physical security together as one unit.
Cyber security is a journey, not a final destination or endpoint. Your aim should be to increase your organization’s cyber maturity and resiliency over time to address the increasingly challenging cyber threat landscape as described in the first series. For a review of what this landscape looks like, read the first article of our series here. Many operators focus solely on the technological aspect of cyber security. Technology is just one of three components that together create a stable approach to cyber security management. In addition to technology, the people involved and the processes of implementing your security measures are all important in creating a balanced cyber security approach, or “cyber stool.”
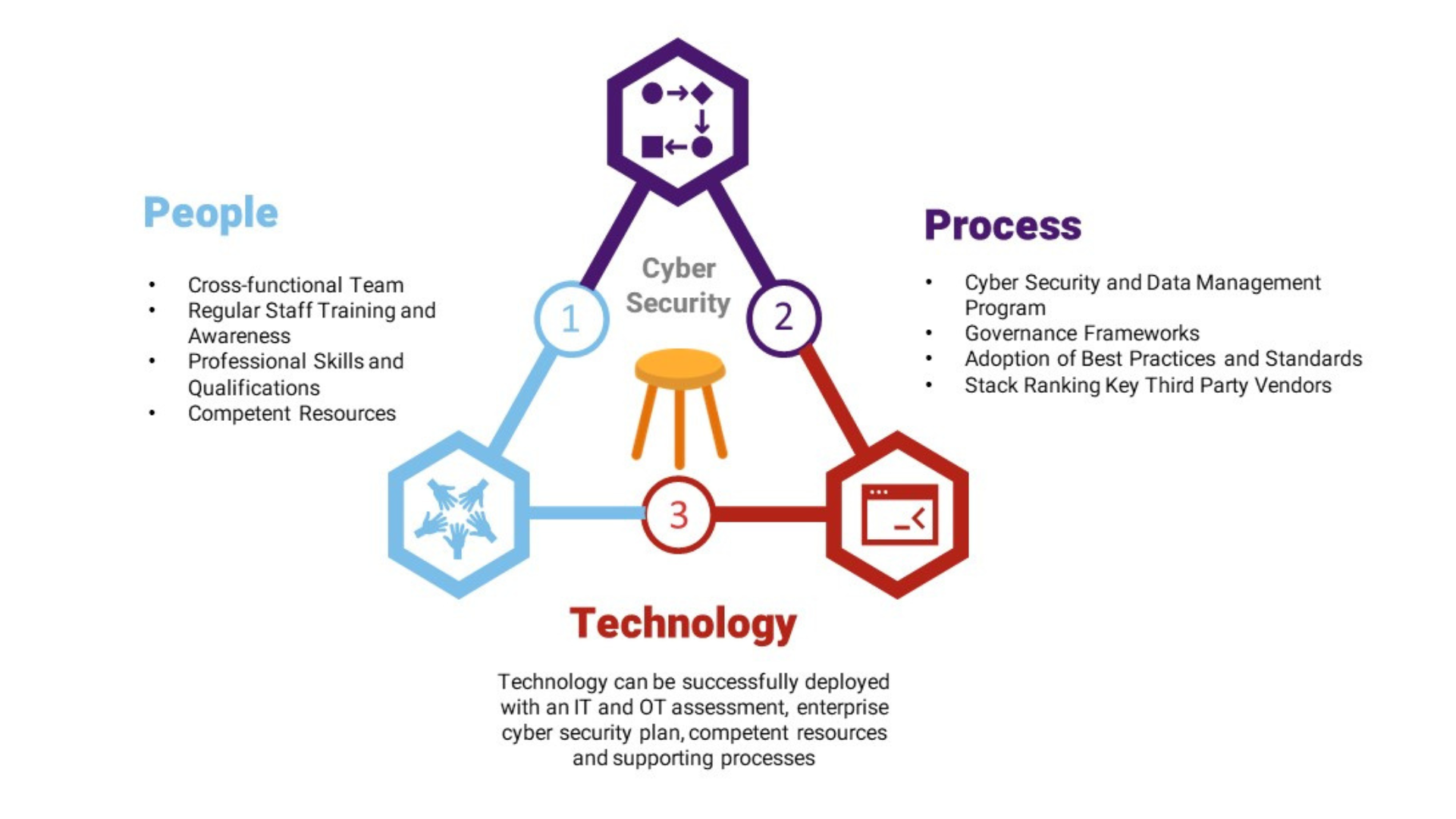
Fundamental Cyber Hygiene
To help maintain the integrity and functionality of your cyber security measures, there are six fundamental elements to consider for your cyber security program:
1. Engage a cross–functional team
Since cyber security is not an strictly an IT issue, a cross-enterprise team is required to develop and manage the program. Establish a Cyber Security Manager to bring together the insights and expertise of cross–functional groups, such as those shown below:
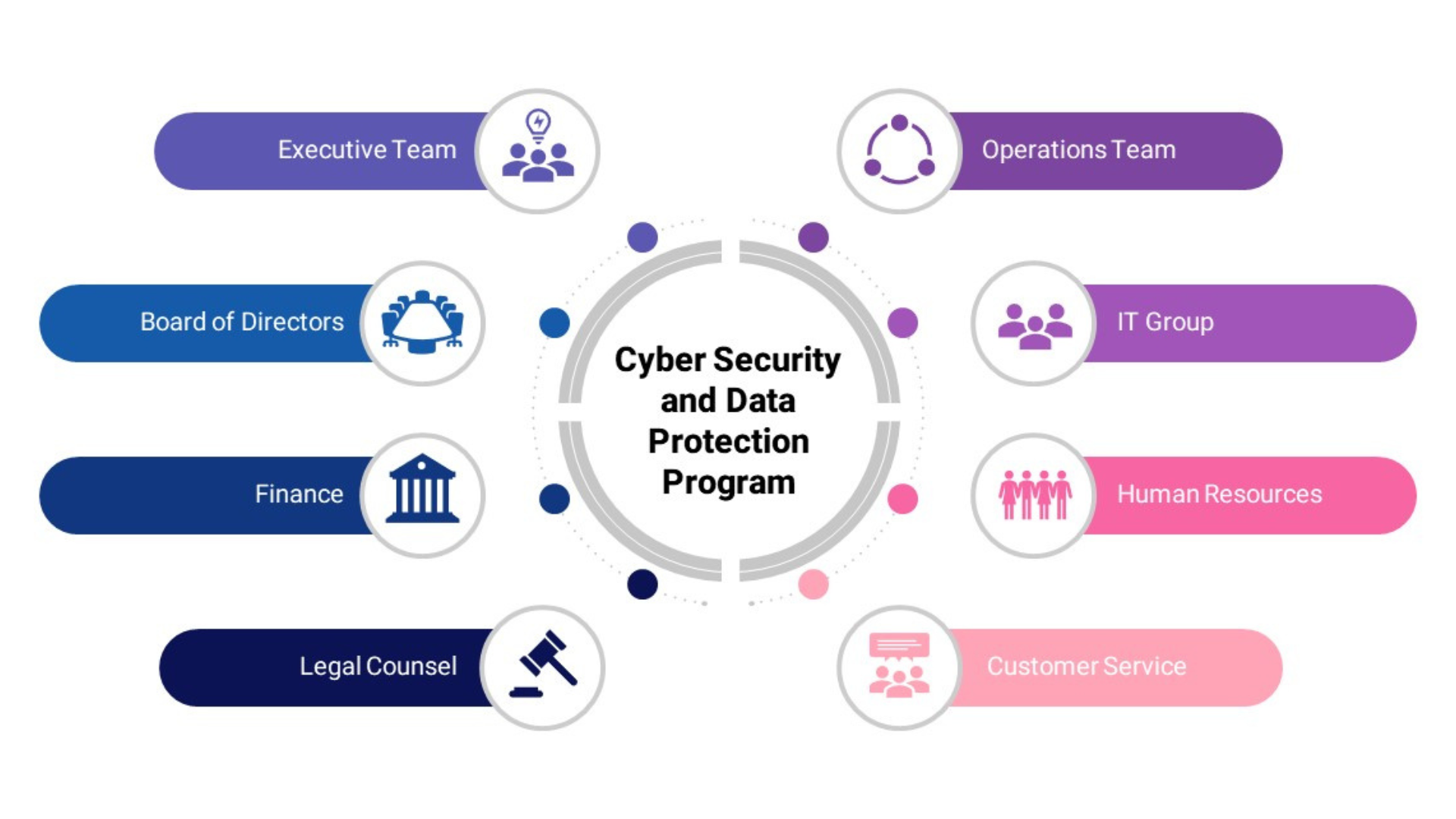
2. Adopt standards
There are many industry-wide standards that you can reference in your cyber security program. Acumen recommends the use of the NIST Cybersecurity Framework as this is a holistic framework covering corporate, IT and Operational Technology (OT) environments[1]. This framework was developed specifically for critical infrastructure and applies well for entities of all sizes. If your entity falls under the NERC CIP regulations, the NIST Cybersecurity Framework can be used as the overarching framework.
3. Balance your efforts across the three legs of the cyber stool
Acumen finds that many entities focus on technology initiatives without paying enough attention to people, governance and process. People are a great source of risk, and governance and process is required to tie the program together for efficiency and effectiveness.
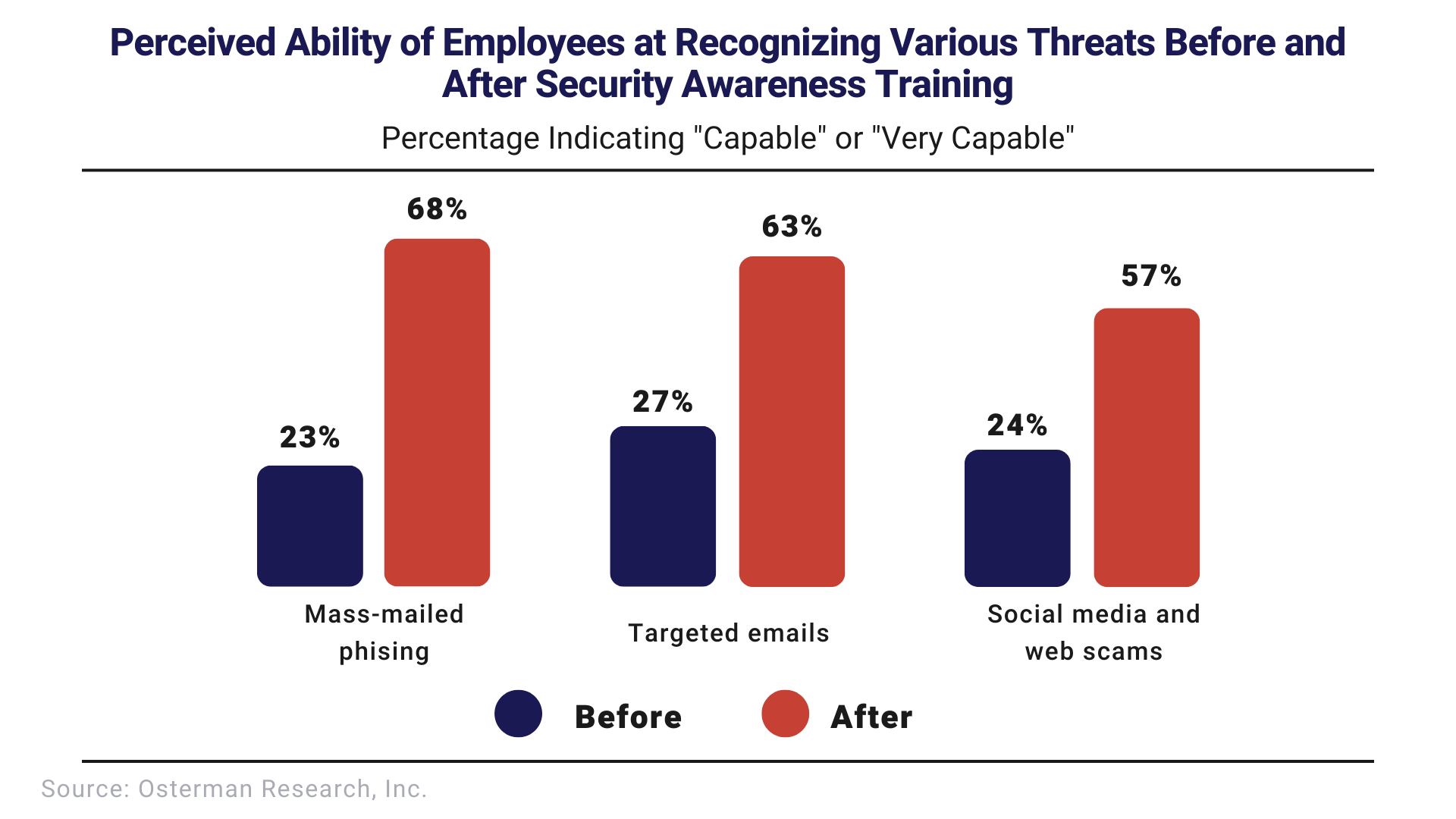
4. Implement regular cyber awareness training
Just like safety training, regular awareness training and vigilance is required for cyber security. Training for employees should be conducted at least quarterly with regular system testing in between trainings. Employees should be encouraged to enhance their training with additional knowledge resources and support should be made readily available. Operations personnel should be provided OT-specific cyber training that focuses on the nuances of and protection from OT cyber breaches.
Operations personnel should be provided OT-specific cyber training that focuses on the nuances and protection from OT cyber breaches.
Develop and test Respond & Recovery Plans
Time is money in a cyber breach. With a thoroughly developed and tested Respond & Recovery Plan, recovery efforts will take less time and result in less cost, operational damage, and reputational damage.
Acumen recommends the development of specific playbooks to explain the process for specific breaches, such as ransomware, data/information theft, and operational breaches.
6. Establish and manage cyber security obligations of your key third parties
It is Acumen’s opinion that the number of risks associated with third parties now surpass insider risks. Third parties represent a challenging set of risks since vendor products and services are so key to the operations of critical infrastructure entities. Increasingly, threat actors are using third parties as “pivot points” to gain access into their intended target – the customers of the third party.
Acumen recommends that you stack rank your vendors from a criticality/risk perspective and apply the following to those key vendors:
- Access the cyber posture of the third party.
- Ensure secure access of third parties into your environments.
- Capture the cyber security obligations of your key vendors in agreements/contracts.
- Conduct Respond & Recovery tests with your key vendors.
Insurance
Cyber insurance is not a substitute for a strong and effective cyber security program, but insurance provides a very valuable form of residual risk protection.
Insurers will want to see evidence of strong cyber hygiene before providing insurance to a critical infrastructure entity. We recommend you find a broker that understands your business and is willing to work with you to source the appropriate insurance coverage.
Summary
The cyber risks associated with a critical infrastructure entity are significant. Without proper implementation and governance of an effective cyber security program, the business, operations, and reputation of your entity can be greatly impacted.
The last part of this series, to be released in early October, will describe proven techniques on how to implement cyber security governance practices.
Acumen’s Cyber & Physical Security Risk Management Services

Acumen offers a full spectrum of Cyber and Physical Security Risk Management Services , including risk identification and prioritization, risk management program development, governance alignment, resourcing, budgeting, and training. We assist our clients in managing cyber and physical security risk via a cost-effective and pragmatic approach. We work as an extension of your team as a trusted advisor, providing industry and threat landscape updates and advice on how to increase your cyber security maturity.
As an Industry Trusted Advisor, Acumen can assist you. For more information:
Sources:
| ↑1 | Cybersecurity Framework | NIST |
|---|





