Protecting Your Assets using Holistic Security Solutions
Similar to the cyber security attacks that have been experienced by many electric utilities, physical security threats are also on the rise. As stated in the news, attacks on electrical systems were up by nearly 80% in 2022 compared to the previous year.

The Physical Security Threat Landscape
Similar to the cyber security attacks that have been experienced by many electric utilities, physical security threats are also on the rise. As stated in the news, attacks on electrical systems were up by nearly 80% in 2022 compared to the previous year.
Prominent examples of this are the Pacific Gas and Electric Company's Metcalf transmission substation shooting in 2014, more recently the coordinated attack in North Carolina on two electrical substations, and an incident in which the FBI said it foiled an alleged plot to attack multiple substations and transformers around Baltimore (PBS). These also follow recent physical attacks on electrical stations in Oregon and Washington.
“This typically very primitive style attack equals millions of dollars in damage,” Brian Harrell, a former US Department of Homeland Security Assistant Secretary for Infrastructure Protection, told CNN. “If you were to shoot out some very key components you can quickly create an effect where this large multimillion dollar transformer becomes essentially a paperweight.”
This, combined with the many attacks on substations related to copper theft, which sometimes results in power outages, clearly shows that physical security threat has become a major concern for critical infrastructure facilities. Advanced threat actors will use a combination of a physical breach coupled with a cyber breach to maximize the overall impact of the attack.
End-To-End Physical Security Services Provided by Acumen, Paladin and Util-Assist
To address and minimize potential physical security threats and vulnerabilities, AESI-US, Inc. (Acumen) provides a holistic approach to both Cyber and Physical Security. In partnership with Paladin Technologies and Util-Assist, our team provides an end-to-end physical security solution for utilities to manage and minimize their physical security risk. A strong physical security program enhances, mitigates, and supports the resilience of an organization in the face of adversity.
A holistic physical security solution includes:
- A Physical Security Assessment to identify any threats and vulnerabilities
- The development of a Physical Security Plan (PSP) which provides practical physical security solutions and mitigations to address the identified threats and vulnerabilities
- The implementation of the PSP, which includes but is not limited to, physical security solutions such as:
• Physical security monitoring and control
• Live video surveillance
• Development of physical security governance, strategies, standards and policies and procedures
• Physical security training - On-going continued assessment and monitoring to ensure the physical security solutions are effective - Deter, Detect, Active Deterrence, and Defend.
- Integration with the cyber security program for a holistic approach to security.
Physical Security Threat and Vulnerability Risk Assessment
A Physical Security Threat and Vulnerability Risk Assessment (PSA) examines the overall physical security of facilities and buildings, specific equipment within the building’s facilities, and the geographical locations of the facilities, while factoring in key business objectives.
The objectives of conducting a PSA are to ensure that the following items are not impacted due to a physical security breach:
- Financial Stability (this refers to the financial stability of the entity in the event of a physical breach which would disrupt operations - based on a physical security risk, what would the financial risk be to the entity?)
- Safety of the entity’s personnel, facilities and the public
- Safety of the public due to the compromise of the entity’s IT and OT systems and/or facilities
- Operational Continuity
- Public Image and Perception
Benefits of a PSA
While many benefits of performing a PSA are self-evident, such as identification of major security vulnerabilities (i.e., unlocked doors, unsecured perimeters, lack of physical access controls, ineffective lighting, CCTV and guarding processes), other findings can reveal blind spots that may be woven into the culture of an organization.
Case Study: While performing an on-site physical penetration testing of office locations, it was discovered that the staff lacked training and awareness on confronting strangers in their office. Their natural sense of hospitality overrode the need for diligence with unknown intruders. By having a third-party, vendor neutral consultant perform the PSA, the client benefited from seeing their organization from an antagonist’s vantage point and quickly provided the appropriate training.
Many companies install the latest security systems but fail to follow up with training and policies on physical security essentials. While many regulatory bodies request proof or certification of training for employees on security policies, there is also a trend where firms are requesting attestation from suppliers, vendors and other organizations of their security practices in order to contain risk in the firm’s supply chain. A PSA will help demonstrate due diligence and rigor, along with the desire to futureproof the security ‘investment’ by incorporating a maintenance and replacement program.
Physical Security Plan and Solutions
The results of the physical security assessment drive the solutions to mitigate the risk identified, potential threats, and vulnerabilities. Just as with cyber security, the solutions focus on the three key elements for a successful program which are “People,” “Governance & Process,” and “Technology,” as depicted below:
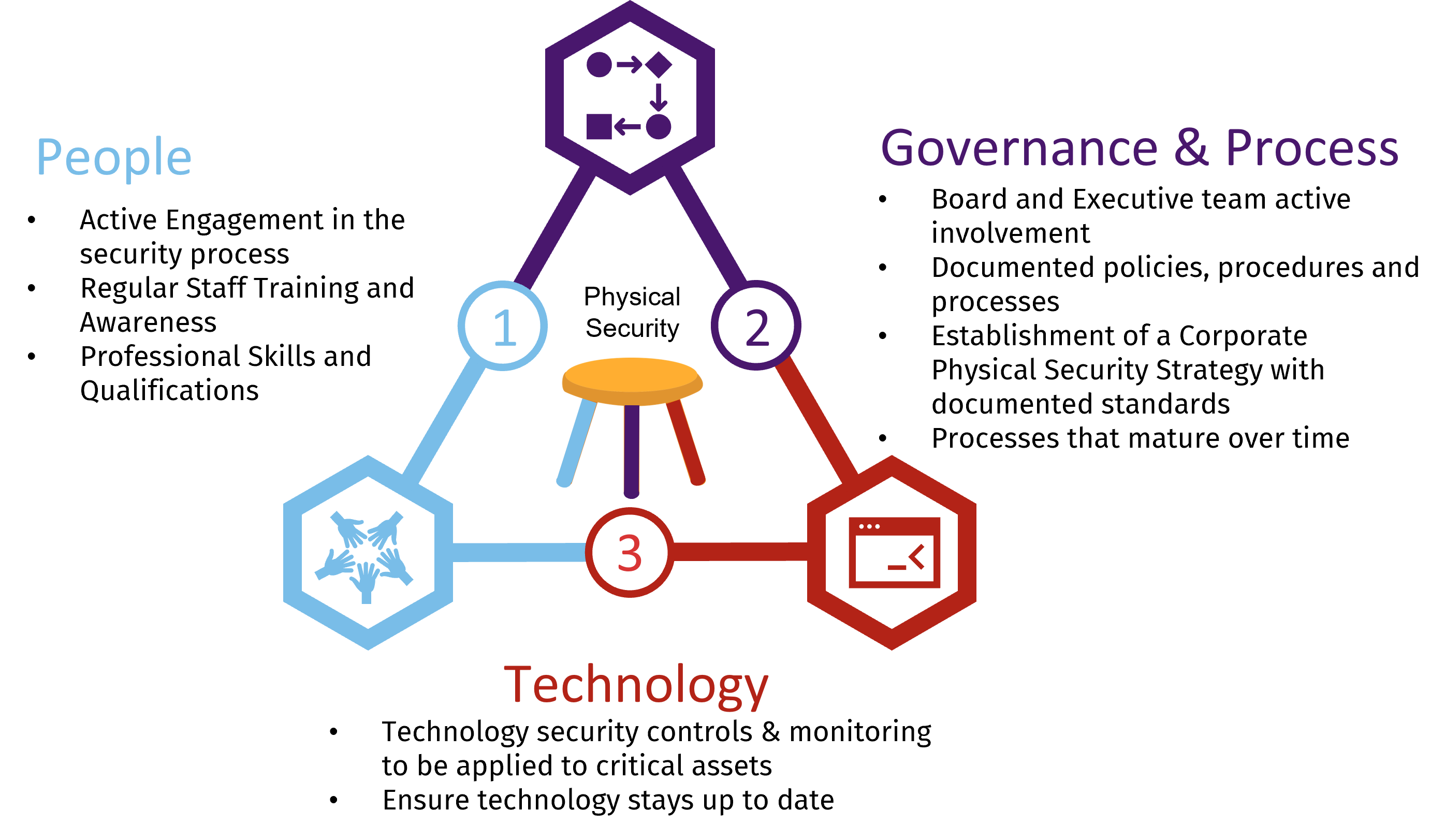
The concept of physical security can be likened to a three-legged stool, where the three legs represent People, Governance & Process, and Technology. Each leg is crucial for maintaining the stability and security of the overall system. If any of these three items fails (see Fig 1), it could destabilize the entire stool and potentially affect physical security, which could result in a financial impact, reputation impact, potential non-compliance, and safety risks of the personnel (including employees, contractors, service providers, vendors, consultants, and the public). Just as a stool cannot stand without all three legs, physical security cannot be fully achieved without the proper integration and alignment of its three key elements.
Physical Security Monitoring
The need for proactive surveillance for critical utility assets in the critical infrastructure sector (Electric, Water/Wastewater and Gas) cannot be overstated. Electricity is considered the most essential of all critical infrastructure, and the utility assets are the cornerstone of a utility to ensuring the safe, dependable, and reliable supply of electricity.
The same applies to the other critical infrastructures, the compromise of the Water/Wastewater and Gas distribution systems can have a major impact on the safety of the public, the entity’s personnel, and facilities.
An intrusion into the facility by unauthorized, typically untrained, or unqualified people is unacceptable for several reasons. A single intrusion can seriously impair the flow of electricity, water and gas, cost tens of thousands of dollars in repairs, cause loss of life or limb, significantly impact the ability of the facility to function, take long lead times to repair or replace equipment, and ultimately tarnish the brand and reputation of the facility owner.
Once physical security controls and video surveillance has been implemented, it is important to ensure that there is active monitoring and not just passive recording for just after-the-fact forensic.
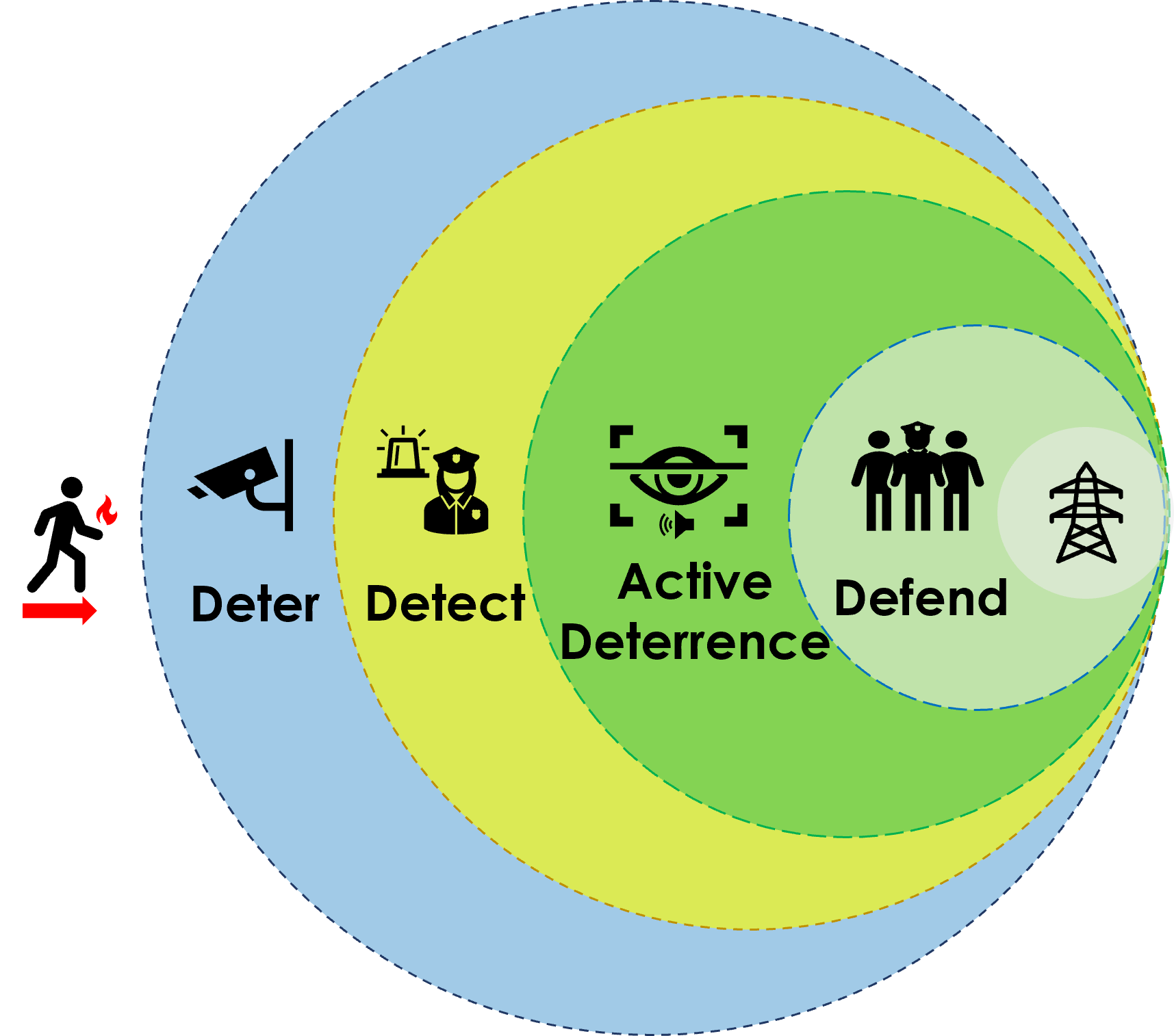
Proactive protection covers four areas of defense-in-depth (see Fig 2): Deter, Detect, Active Deterrence and Defend:
Deter: The obvious presence of cameras, strategically located site lighting, and signage that announces monitoring, acts as an initial deterrent to potential thieves.
Detect: If someone ignores the defense systems in place and intrudes on the facility, AI monitoring recognizes the threat and notifies a security agent.
Active Deterrence: The security operator activates additional deterrents, using security lights and verbal warnings delivered via loudspeakers to make it clear to intruders that they are being monitored in real time.
Defend: In the final line of defense, security operator dispatch police or utility crews to the scene.
Acumen, Paladin Technologies, and Util-Assist offer end-to-end physical security services that help your critical infrastructure identify vulnerabilities and minimize risks.
About Acumen
Established in 1984, Acumen is a privately owned engineering and management consulting firm providing pragmatic and sustainable engineering, technical and management solutions across North America, and internationally. We provide utility management and engineering, cyber and physical security, operational technology, regulatory compliance, utility automation, smart grid, and risk management services to public power utilities, water/wastewater utilities, co-ops, IOUs and IPPs, commercial & industrial (i.e., critical infrastructure), and government-owned entities.
Acumen has a balanced organizational matrix, with permanent staff members who have dedicated over 35 years providing consulting services to over 600 utilities and critical infrastructure operators in North America and internationally. Our team is composed of engineers, technicians, management, and consultants who bring a depth of knowledge and experience from a variety of roles in distribution, transmission, generation, and system operations at utilities across North America. As a result, we are intimately familiar with the needs and financial/operational realities of various utility types, including cooperatives, municipalities, government/public utilities, investor-owned utilities, independent power producers, and more.
With a large portfolio of clients spread across the USA, Acumen employs staff in various states across the country that work remotely or on-site at client facilities as needed.

Acumen is the Hometown Connections Partner for cyber and physical security services, regulatory services, and IT/OT services for public power and their associated municipalities. As such, Acumen has worked extensively over the years with Hometown, the American Public Power Association (APPA), Joint Powers/Action Agencies, and public power utilities and their associated municipalities to deliver value. Tim Blodgett, past CEO of Hometown Connections can attest to Acumen’s experience, capabilities, and value proposition for municipal entities.
Acumen has been engaged in conducting physical security risk assessment, developing corporate physical security strategies and governance, as well as developing physical security plans (PSP) and roadmaps to mitigate the risk identified, potential threats, and vulnerabilities to meet the North American Electric Reliability Corporation (NERC) standards as they pertain to Physical Security, and the physical security requirements in California as set forth by the California Public Utilities Commission (CPUC).
For more information, visit www.aesi-inc.com
About Paladin Technologies
Paladin Technologies has emerged as one of the largest complex systems integrators in North America. Paladin specializes in the design and installation of Network Infrastructure, Audio Visual, Fiber Optics/OSP, Structured Cabling, Integrated Security, DAS, and more.
With over 1,500 employees across 34 offices, Paladin’s technical resource force enables their teams to deploy solutions in remote locations across North America and to deliver seamless technology solutions for national, multi-site clients. The team holds manufacturer-trained technicians, PMP-certified project managers, CTS- and RCDD-certified design engineers, coordinators, and administrative resources.
Leveraging strong manufacturer relationships, Paladin can champion on behalf of clients to ensure elite discounts and supply chain access. These factors combine to create a unique value proposition that does not compromise between cost and quality. Furthermore, with in-house expertise in leading technologies, Paladin has positioned itself as a single point of contact for accountability and best practices when designing, implementing, and managing physical security systems for Critical Infrastructure facilities in order to meet corporate requirements and regulatory requirements such as the NERC CIP Standards.
Although environments are ever-changing, Paladin’s continued experience with physical security regarding critical infrastructure has enabled Paladin to refine and align with exclusive advisors to ensure clients achieve objectives while reducing all aspects of risk, including regulatory, operational, and security related.
For more information, visit www.paladintechnologies.com
About Util-Assist
Established in 2005, Util-Assist is helping shape the utility of the future. Util-Assist's solutions merge technology with strategy to streamline processes, boost productivity, enable data-driven business decisions, and deliver enhanced customer experiences, transforming how utilities operate and deliver value to their customers. We understand the utility perspective and have developed innovative, compelling solutions to address utility needs, increase efficiencies, and ensure best value.
Our managed services include SecureAssist AI-enabled substation surveillance. With its defense-in-depth design, the physical security monitoring service delivers multiple protective layers to keep utility critical infrastructure facilities secure. Like an impregnable castle with a moat, towers, and a drawbridge, if one layer of security fails, another line of defense is in place to prevent an intrusion. AI algorithms accurately distinguish between objects, such as a person, an animal, and a vehicle, and eliminate false alerts by instantly confirming events that can be ignored, like fallen branches or inclement weather. SecureAssist combines best-in-class technology in a single solution, all at a very cost-effective price. If a system or cameras are already in place, SecureAssist will easily integrate with existing or preferred monitoring equipment.
For more information, visit www.util-assist.com
The combination of Acumen, Paladin and Util-Assist’s experience cover the following areas:
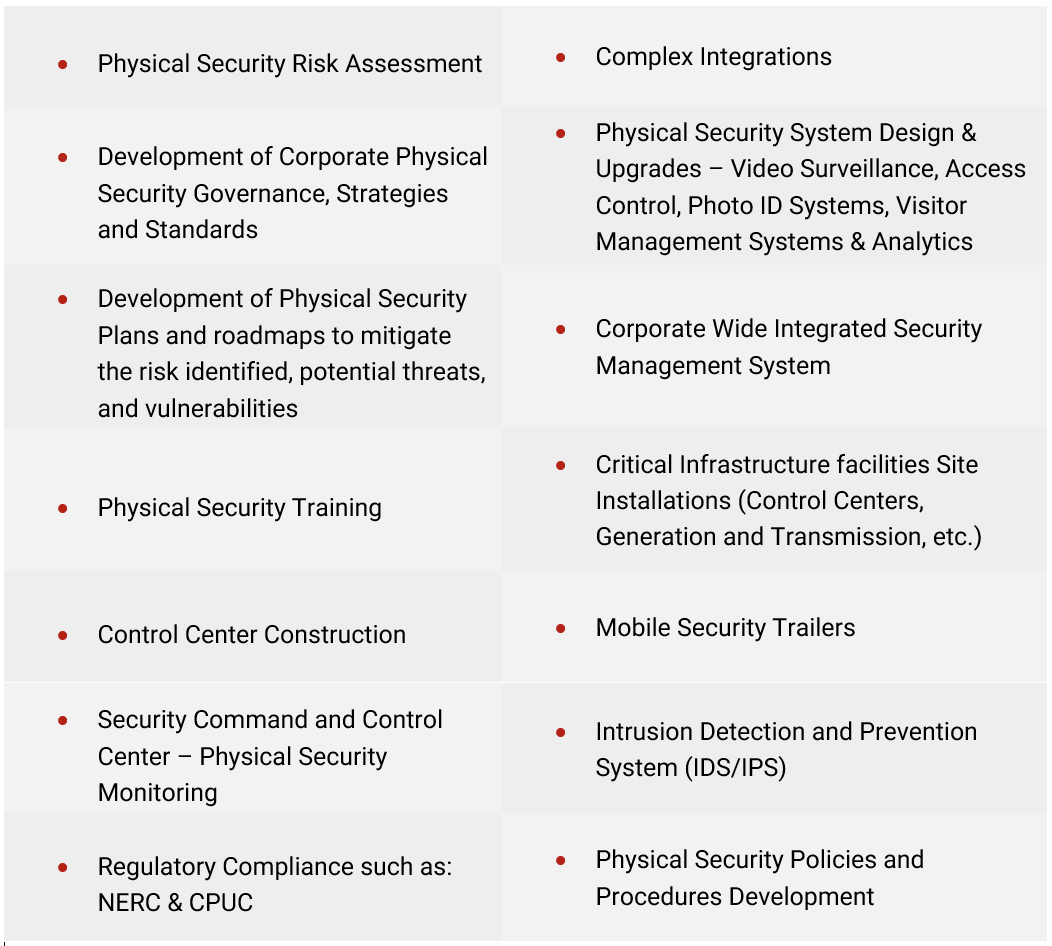
We provide a physical security assessment, create a physical security plan, develop and implement solutions, and continuously assess the efficacy of our solutions. By working with us, you can ensure financial stability, protect the safety of your personnel and the public, maintain operational continuity, and improve public perception. Click below to book a free consultation with us today!






