Quantifying the Financial Impact of Cyber Breaches in the Utility Sector

Utility CxOs ask the question: how do you quantify the potential financial impact of cyber breaches?
This has been a long-standing challenge in the utility sector and one that can lead to frustration for IT and OT leaders who often struggle to justify cyber security budgets. Utility CxOs intuitively understand that a cyber breach can lead to financial loss, service disruption, and/or the long-term cost impact of reputational damage, but they need further quantification to be able to confidently approve budgets and also to secure the proper cyber insurance coverage.
So how do you quantify the financial impact of cyber breaches? The short answer is that it is an art and a science.
In my work with utility clients, I use several approaches to develop this quantification as described below.
Different Approaches, One Goal
As a starting point, I map the utility’s attack surface on a one page visual. The cyber-attack surface is a military concept that identifies the areas of vulnerability and risk that can be exploited. Supply chain/third party and insider risks are examples of risk areas. It is important to define the risk areas that pertain to your utility for further quantification.
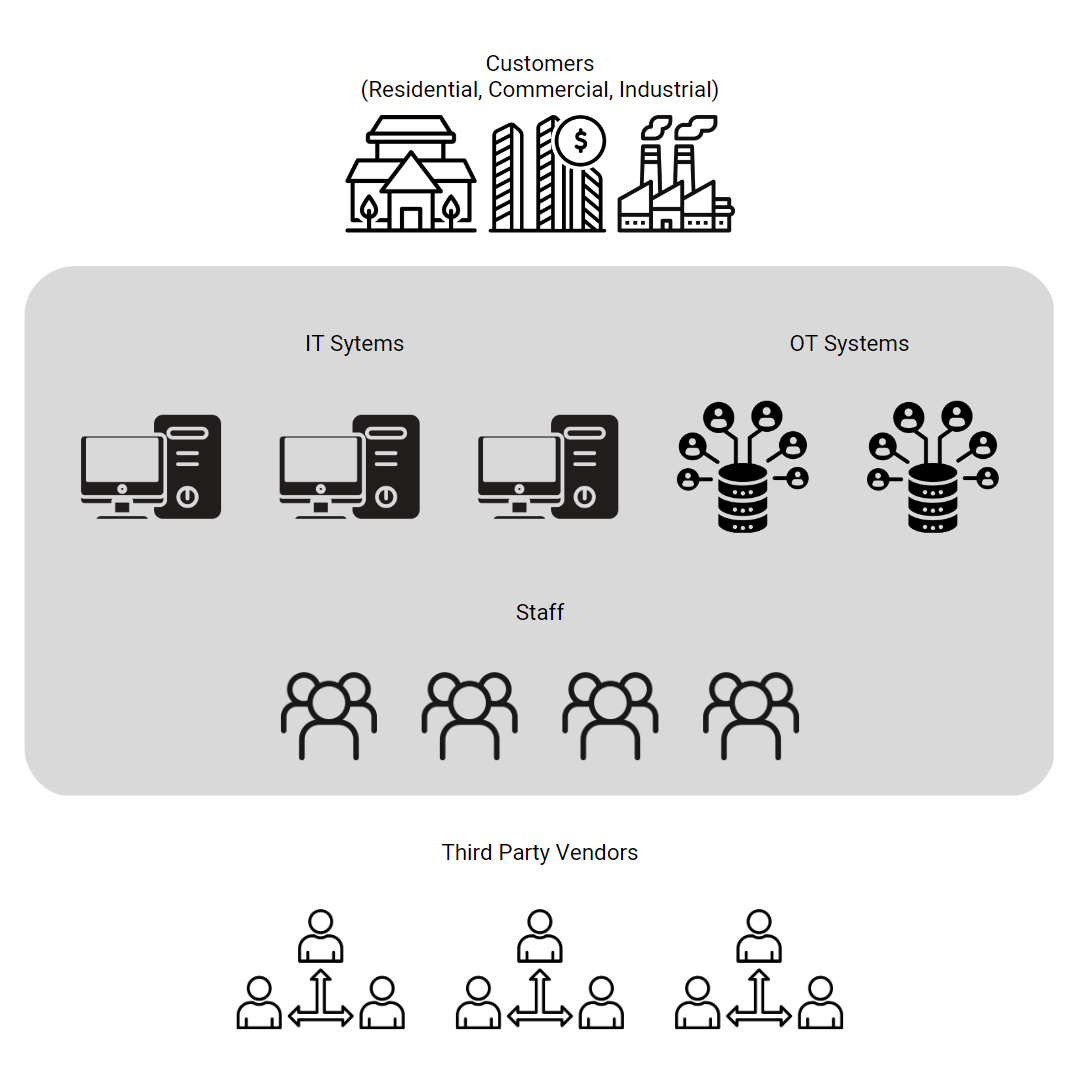
If you use Heat Maps in your risk management process, the identified risk areas can be visually populated on a Heat Map using risk and impact approximations.
For more specific quantification I use the following approaches:
- Obtain publicly available ransomware cost information. This cost information will provide a good financial proxy as ransomware is currently the most prevalent form of cyber breaches for utilities.
2. Obtain information from your insurance broker. Many insurance brokers such as Marsh (Marsh | Global Leader in Insurance Broking and Risk Management) have good financial impact models that they can share with you, as well as information on average insurance spend by sector.
3. Identify internal and external costs and quantify those costs. I use the Accenture/Ponemon Cost Framework Model shown in their Ninth Annual Cost of Cybercrime report to estimate these costs.
In this model, the internal costs include:
- Detection
- Investigation
- Containment
- Recover
The external costs include:
- Information loss of theft
- Business disruption
- Equipment damage
- Revenue loss
For all of the categories above I estimate both OPEX and CAPEX costs and then total the costs.
The three approaches will most likely result in different values, representing a range of potential financial impacts.
Now the art form comes in. Review the cost estimates using the approaches listed above, and then determine a financial impact range that feels reasonable for your utility. This can be done with experience and a good perspective on your operations.

Summary
Select the financial impact approach or approaches that work best for your risk management process, and you will have a better perspective on the potential financial impact of cyber breaches. Review the results on a regular basis given that the cyber threat landscape for utilities is continually becoming more challenging and more impactful.





