Decoding Sandworm's Tactics: Unveiling the Cyber-Physical Attack on Operational Technology
Sandworm, a notorious hackergroup, poses significant threats to Operational Technology (OT) systems. In a recent cyber-physical incident analyzed by Mandiant, Sandworm's innovative techniques disrupted critical infrastructure, raising global concerns about OT security.

In the ever-evolving realm of cyber threats, Operational Technology (OT) systems have emerged as prime targets, sparking concerns about critical infrastructure security across energy, manufacturing, transportation, and utilities. A recent report from Waterfall Security Solutions has chronicled 57 OT cyber incidents with physical consequences out of 218 reported attacks, highlighting the growing challenges OT systems face globally.
Amidst this landscape, the notorious hacker group Sandworm stands out as a significant player. Drawing inspiration from the science fiction series Dune, Sandworm subtly weaves references to the revered Sandworms of the desert planet Arrakis into its code. This homage adds an element of intrigue to Sandworm's activities, particularly concerning operational technology (OT) security, prompting global concerns. Sandworm operates as a nation-state threat actor, utilizing aliases like Telebots and Iron Viking. Over the last decade, Sandworm has been a critical player in cyber campaigns, particularly targeting Ukraine. Renowned for disruptive attacks, including the infamous 2015 Ukraine power grid incident and the 2017 NotPetya malware assaults, Sandworm's influence extends globally, showcasing the extensive ambitions of its backing military. Recent actions, such as the April 2022 attempt to blackout Ukraine using the Industroyer2 malware, highlight Sandworm's continued evolution.
This juxtaposition highlights the dual challenges OT systems face — the persistent threats they encounter and the specific menace posed by formidable entities like Sandworm, drawing attention to the intricate dance between cybersecurity measures and evolving cyber threats in operational technology.

Exploring the Cyber Threat Actor Sandworm
In a significant cyber-physical incident, Sandworm directed its efforts towards a Ukrainian critical infrastructure organization, orchestrating a multi-event cyber attack with innovative techniques impacting industrial control systems (ICS) and operational technology (OT). Unfolding from June to October 2022, the attack involved OT-level Living off the Land (LotL) techniques, leading to an unplanned power outage coinciding with missile strikes on Ukrainian critical infrastructure. The introduction of CADDYWIPER in the IT environment exacerbated disruptions, revealing a sophisticated and evolving offensive cyber capability. Sandworm's activities have sparked global concerns about the security of operational technology.
Mandiant's detailed analysis of the 2022 Sandworm cyber-physical incident provides a nuanced understanding of the threat actor's tactics, techniques, and the evolving landscape of offensive cyber capabilities.
Insights from Mandiant's Analysis:
Mandiant's thorough investigation unveiled a sophisticated intrusion that unfolded in June 2022 and climaxed in two disruptive events on October 10 and 12, 2022. While the initial access vector into the IT environment remained unidentified, Mandiant successfully traced Sandworm's progression to the OT environment through a hypervisor hosting a supervisory control and data acquisition (SCADA) management instance. Lateral movement within the SCADA system indicated potential access for up to three months.
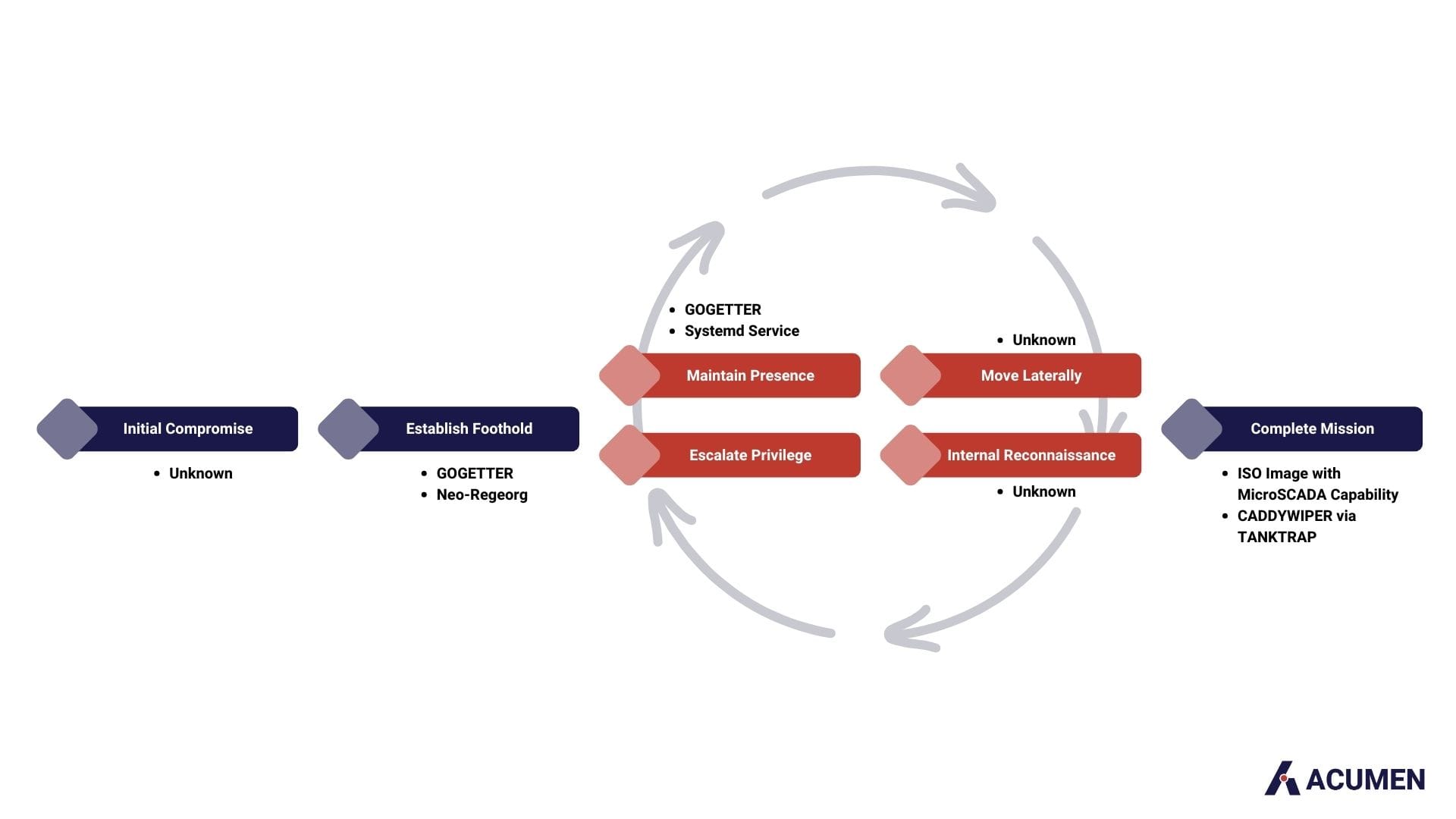
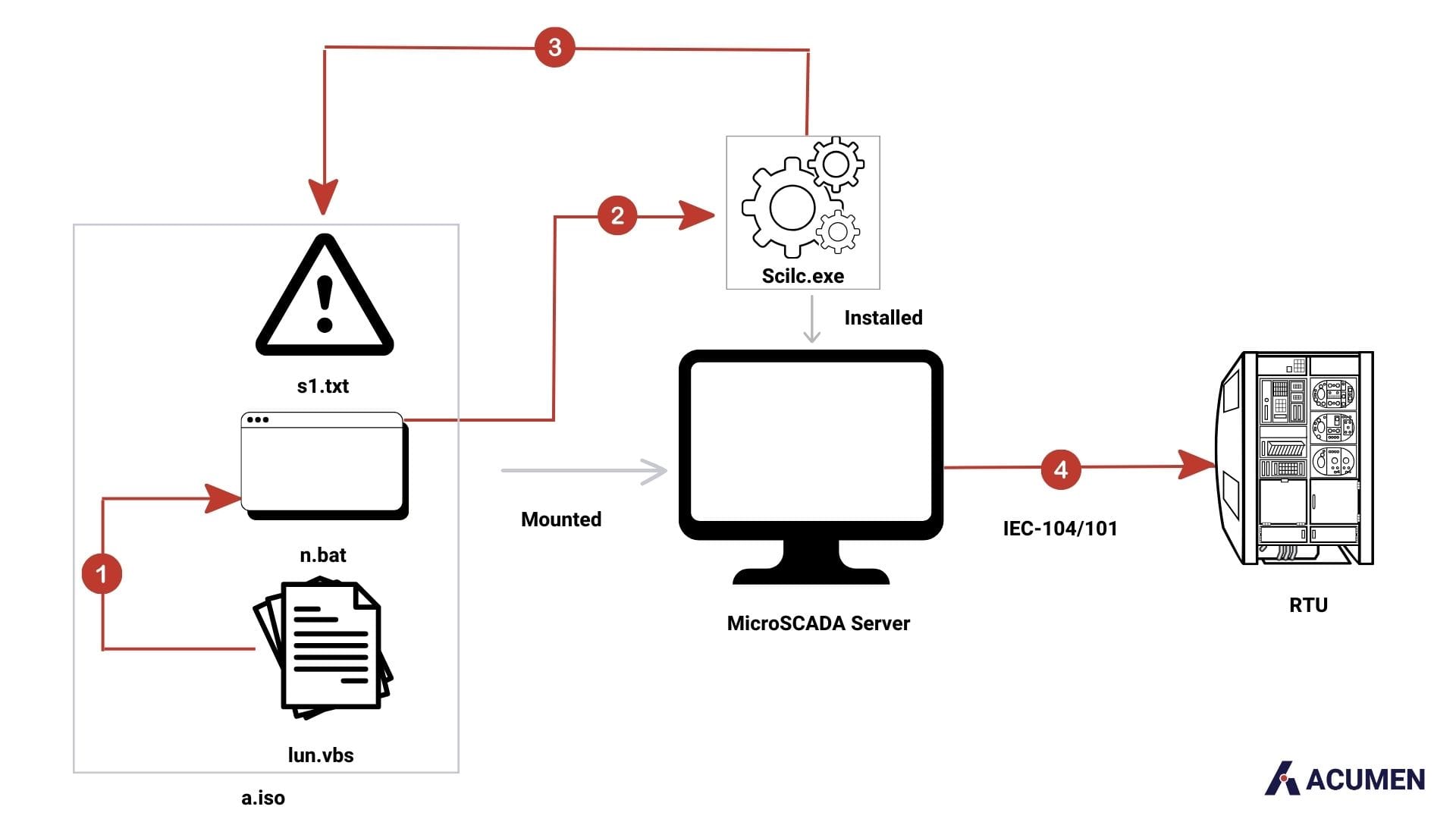
On October 10, Sandworm executed a disruptive OT attack using an optical disc image (ISO) named "a.iso." The attack aimed to execute malicious control commands, leading to an unscheduled power outage. Forensic analysis suggested the attacker's capability to potentially manipulate substation equipment, possibly through IEC-60870-5-104 (a standard for TCP/IP-based communications) or IEC-60870-5-101 (a standard for serial connections) protocols, crucial in managing industrial control systems within electric power networks.
Two days later, Sandworm showcased a dual-pronged strategy by deploying a new variant of CADDYWIPER. This disruptive wiper is focused on making data irrecoverable and causing maximum damage within an environment in the victim's environment, disrupting both OT and IT systems.
In June 2022, Sandworm's initial compromise involved deploying the Neo-REGEORG, an enhanced iteration of the publicly available REGEORG project. Neo-REGEORG is a web shell generation tool designed to establish a SOCKS proxy on the compromised system. Subsequently, the deployment of GOGETTER, a Golang-based tunneler, facilitated lateral movement. Systemd service units were employed to maintain persistence, ensuring the execution of the GOGETTER binary on system reboot.
The distinctive aspect of the attack unfolded in Sandworm's lateral movement to the SCADA hypervisor, where the OT attack occurred. This technique impacted the OT environment by executing code within an End-of-Life (EOL) MicroSCADA control system. The attacker manipulated connected substations by employing SCIL programming language commands through the native scilc.exe utility. SCIL, designed for MicroSCADA systems, enables various operations through text-based commands. Executed within the MicroSCADA software suite, specifically in the "\sc\prog\exec" folder, the native scilc.exe utility played a central role. Although specific SCIL commands remain undisclosed, this method allowed precise control over the MicroSCADA system, impacting the victim's substations.
This incident illuminates the rogue nation's sustained investment in offensive cyber capabilities, particularly in the OT domain. Sandworm's streamlined approach and the shift towards lightweight, generic Living off the Land (LotL) techniques, a strategy where attackers use pre-existing tools and built-in system functionalities to carry out malicious activities, underscore an increased tempo of wartime cyber operations. The coordination with the kinetic operations of a certain nation-state suggests strategic synchronization.
Historical activities with a nexus to this nation-state impacting OT emphasize the global threat Sandworm poses. Asset owners worldwide, especially those utilizing MicroSCADA products, are urged to promptly mitigate the demonstrated tactics, techniques, and procedures against IT and OT systems.
Strengthening Detection and Segmentation Measures
Early detection and effective recovery are paramount in the realm of cyber-physical attacks. Swift identification of anomalous activities can mean preventing a devastating incident and succumbing to its consequences. Sandworm's sophisticated cyber-physical attack against Ukrainian critical infrastructure underscores the need for robust early detection measures. The attacker's ability to navigate seamlessly through IT and OT environments highlights the importance of implementing network segmentation. By segmenting these environments, organizations can hinder lateral movement, making it significantly more challenging for attackers to compromise critical systems. Anomaly detection and continuous monitoring play a crucial role in recognizing deviations from normal behavior, providing a proactive defense against potential intrusions. Furthermore, stringent access controls and privilege management help limit the attack surface, reducing the likelihood of adversaries gaining unauthorized control. Implementing a well-prepared incident response plan and regular backups ensures that organizations can recover swiftly and minimize downtime after a cyber-physical attack.

Structured Recovery Strategy and Vigilant Defense
The aftermath of a cyber-physical attack demands a structured approach to recovery to mitigate the impact and restore normalcy. Sandworm's utilization of known vulnerabilities emphasizes the importance of proactive security patching and updates. Timely application of patches is essential for closing these vulnerabilities, reducing the risk of exploitation. Endpoint protection becomes a critical line of defence against malware introduced through endpoints, a tactic often employed by threat actors. Continuous network monitoring for unusual activities is vital in detecting and responding to post-attack behaviours that may indicate ongoing threats. The development and regular update of an incident response plan and a focus on regular backups form the foundation of a structured recovery strategy, allowing organizations to regain control swiftly in the face of a cyber-physical incident.

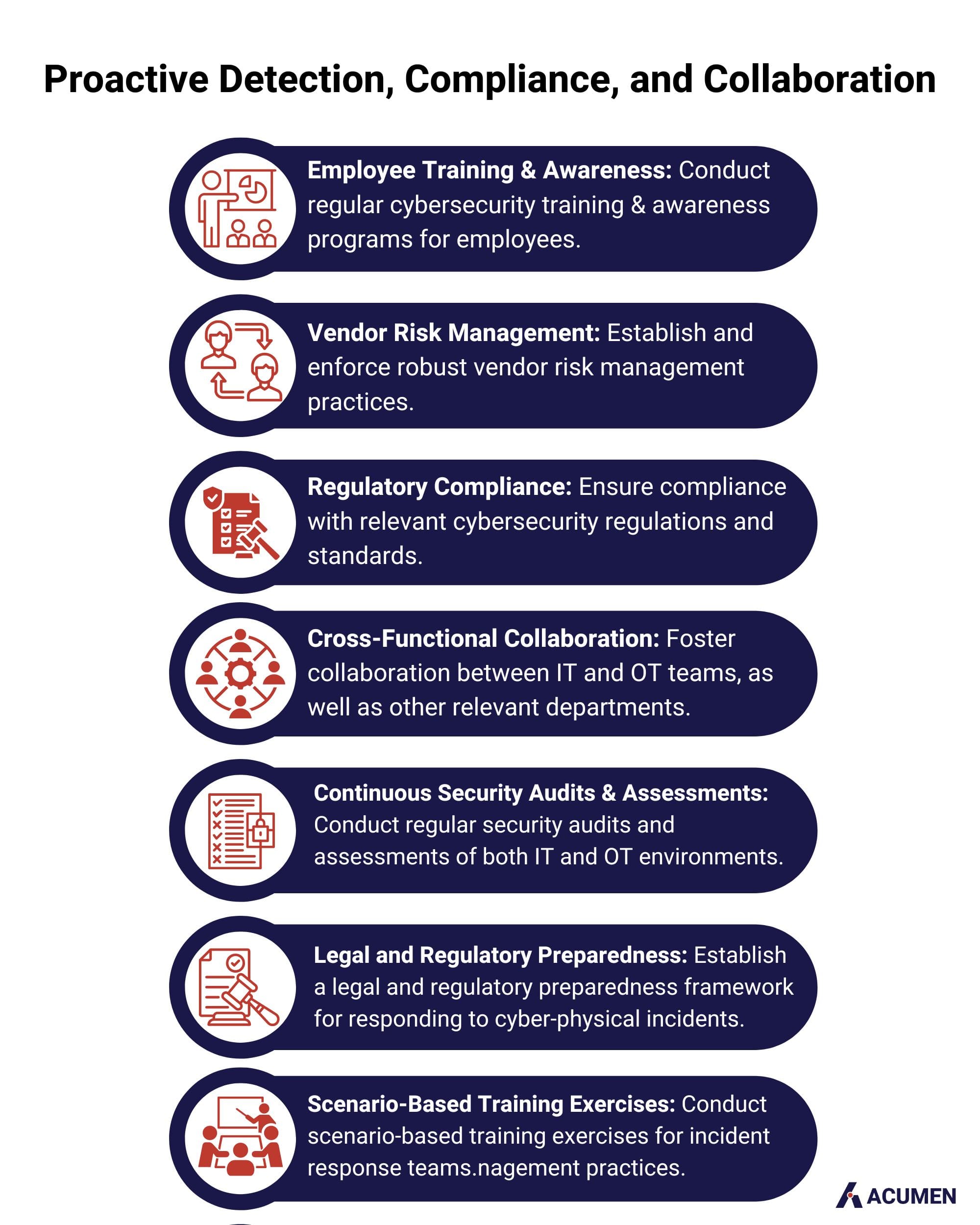
Proactive Detection, Compliance, and Collaboration
Proactive detection and alerting are indispensable components of a comprehensive cybersecurity strategy, especially in the context of cyber-physical threats. Sandworm's use of third-party vendors as potential attack vectors underscores the importance of robust vendor risk management. Ensuring compliance with relevant cybersecurity regulations and standards is essential for establishing a baseline of security measures. Cross-functional collaboration between IT and OT teams is crucial for a unified and coordinated response, minimizing the potential impact of an attack. Continuous security audits and assessments provide organizations with insights into evolving vulnerabilities, strengthening their overall defence. Legal and regulatory preparedness and scenario-based training exercises further enhance an organization's ability to navigate the complexities of cyber-physical incidents.
In conclusion, the threat landscape evolves dynamically as we navigate an increasingly interconnected digital landscape. The cyber-physical attack orchestrated by Sandworm serves as a stark reminder of the critical importance of proactive cybersecurity measures, particularly for safeguarding essential infrastructure. The recommendations outlined—ranging from robust network segmentation to the integration of emerging technologies like AI and blockchain—aim not only to defend against known threats but also to anticipate and adapt to the ever-changing tactics of malicious actors. Organizations can fortify their defences, enhance early detection capabilities, and establish resilient recovery strategies by adopting these measures. As we advance in the digital age, a collective commitment to cybersecurity is indispensable for safeguarding the integrity and functionality of the systems that underpin our modern way of life.
References:
Nugent, J., Castelan, F., Bienstock, D., Moore, J., & Murchie, J.. (2023, July 25). Exploitation of Citrix Zero-Day by Possible Espionage Actors (CVE-2023-3519). Mandiant. https://www.mandiant.com/resources/blog/citrix-zero-day-espionage
Proksa, K., Wolfram, J., Wilson, J., Black, D., Lunden, K., Kapellmann Zafra, D., Brubaker, N., McLellan, T., & Sistrunk, C. (2023, November 9). Sandworm Disrupts Power in Ukraine Using a Novel Attack Against Operational Technology. Mandiant. https://www.mandiant.com/resources/blog/sandworm-disrupts-power-ukraine-operational-technology
Sandworm (hacker group). (n.d.). In DBpedia. Retrieved December 8, 2023, from https://dbpedia.org/page/Sandworm_(hacker_group)
Waterfall Security Solutions. (n.d.). How Are OT Hackers Getting IN Today? Retrieved from https://waterfall-security.com/ot-insights-center/ot-cybersecurity-insights-center/how-are-ot-hackers-getting-in-today/
Zetter, K. (2014, October 14). Russian 'Sandworm' Hack Has Been Spying on Foreign Governments for Years. Wired. https://www.wired.com/2014/10/russian-sandworm-hack-isight/






