The Importance of Addressing Supply Chain Risks in Industrial Control Systems
Recent cyber, such as the X_Trader and the 3CX supply chain attack, have highlighted the importance of addressing supply chain risks in the energy sector (BleepingComputer, 2023).

Recent events, such as the X_Trader and the 3CX supply chain attack, have highlighted the importance of addressing supply chain risks in the energy sector (BleepingComputer, 2023).
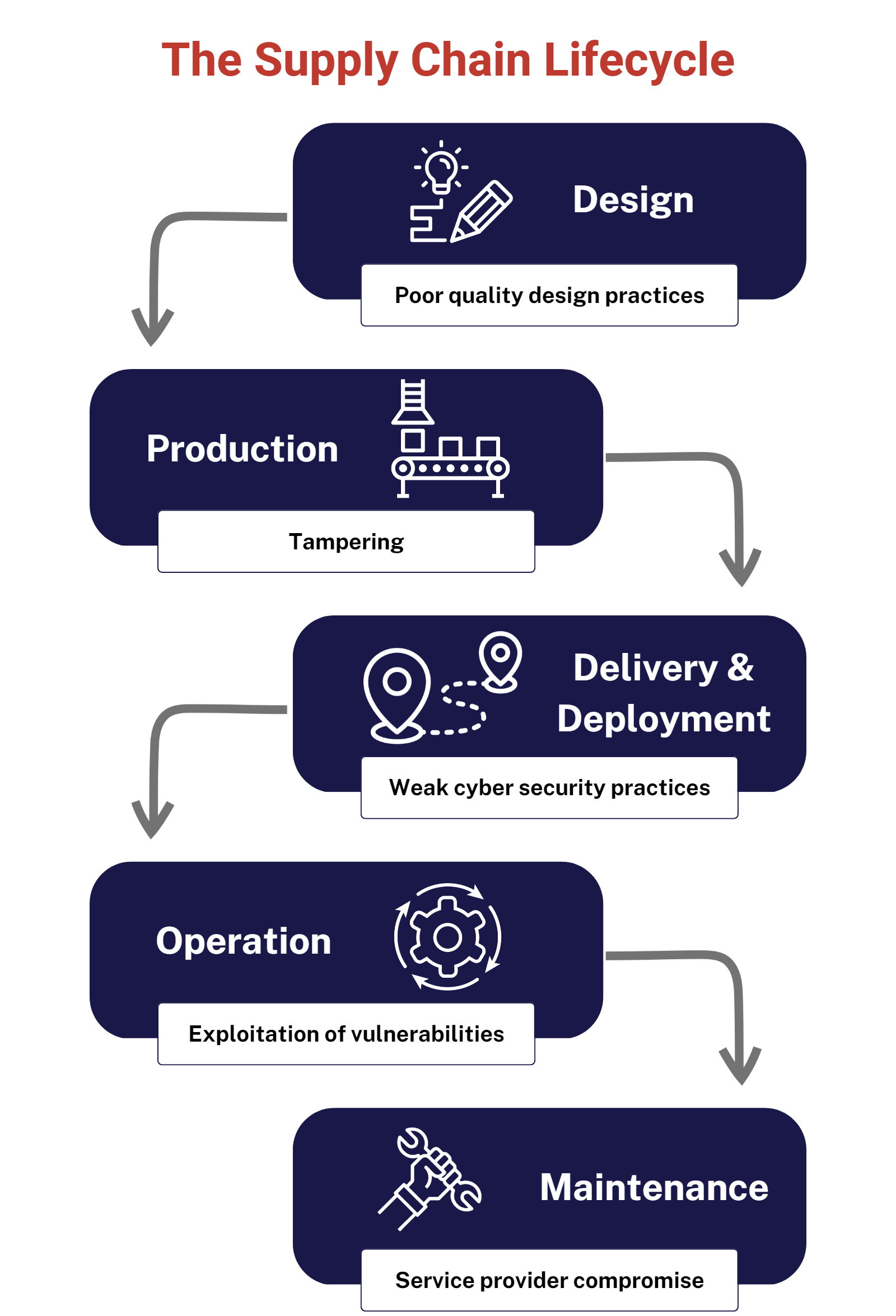
What is a Supply Chain Attack?
A supply chain attack, also known as a third-party or value-chain attack, occurs when threat actors compromise an organization's network by exploiting the vulnerabilities in the connected applications or services provided by outside partners, such as suppliers. The appeal of supply chain attacks for cybercriminals lies in the trust organizations place in their suppliers' applications and services, which have typically been vetted and trusted by security teams and often have access to sensitive or valuable internal data.
In a supply chain attack, adversaries can exploit the trusted relationship between an organization and its suppliers to gain unauthorized access to the target network. Once inside, they can steal, encrypt, or destroy critical data, costing companies millions in repair costs and reputational damage. These attacks are incredibly challenging to detect and prevent due to the interconnected nature of modern supply chains, with third-party suppliers often using software from other business partners, who in turn have their own outside connections. This creates a complex web of relationships, making it harder for organizations to identify and address potential threats.
Several high-profile supply chain attacks in recent years, including the SolarWinds and Kaseya incidents, caused significant disruption to thousands of organizations worldwide. With an increasing reliance on digital supply solutions and the growing complexity of application environments, experts predict that supply chain attacks will continue to rise, making it crucial for organizations to enhance their security and risk management strategies to better protect against such threats.
The X_Trader Supply Chain Attack:
The X_Trader supply chain attack resulted from the compromise of Trading Technologies' X_Trader software installer. According to Symantec's Threat Hunter Team, this breach led to the subsequent compromise of the 3CX Desktop App and has also impacted several critical infrastructure organizations in the United States and Europe, including at least two in the energy sector. The attackers used a trojanized installer for X_Trader software to deploy a multi-stage modular backdoor onto victims' systems. Once installed, the malware could execute malicious shellcodes or inject a communication module into web browser processes running on compromised systems. The compromised energy sector organizations were targeted by the malicious X_Trader installer between September and October of 2022, as reported by Symantec. The compromise of critical infrastructure targets is a concern, given that Nation-State-backed hacking groups are also known for cyber espionage. In addition, it cannot be ruled out that strategically important organizations breached during a financial campaign are targeted for further exploitation.
This attack demonstrates the growing risk and potential impact of supply chain attacks on strategic organizations and critical infrastructure.
Best Practices to Protect Against Supply Chain Attacks
- Conduct thorough risk assessments: Regularly assess and evaluate your organization's cybersecurity posture, including the potential risks associated with third-party vendors and supply chain partners. This includes assessing their security practices and ensuring they meet your organization's standards and compliance requirements.
- Implement a third-party risk management program: Develop a comprehensive third-party risk management program that includes regular monitoring and evaluation of your suppliers' security practices. This should involve breaking down internal operational silos and ensuring that all departments are on the same page regarding protection.
- Adopt a zero-trust framework: Implement a 'never trust, always verify' security framework that requires all applications and services, including those from trusted suppliers, to pass authentication checks before gaining access to your network.
- Inventory and monitor third-party tools: Keep an up-to-date inventory of all third-party tools used by your organization and monitor them for vulnerabilities and disclosed breaches. This will help you stay informed about potential threats and take necessary action when needed.
- Implement network segmentation: Divide your network into smaller segments to limit the potential damage of an undetected attack. This will make it more difficult for attackers to access higher-value corporate resources and spread laterally across your network.
- Ensure strong identity and access management: Strengthen your identity and access management practices, including implementing multifactor authentication, continuous monitoring, and stringent identity onboarding procedures.
- Regular penetration testing and vulnerability scanning: Conduct regular penetration tests and vulnerability scans to identify and remediate any weak points in your supply chain security.
- Encrypt sensitive data: Identify and encrypt highly sensitive data within your organization to reduce the potential impact of a successful supply chain attack. Even if attackers gain access to your systems, they won't be able to leverage encrypted assets.
- Maintain up-to-date security technologies: Utilize cutting-edge security technologies such as endpoint detection and response (EDR), network detection and response (NDR), and user behavior analytics (UBA) to detect and respond to potential threats.
- Develop an incident response plan: Create a comprehensive incident response plan that includes procedures for dealing with supply chain attacks. This should involve immediate steps to identify and contain the attack, as well as longer-term strategies for mitigating the risk of future incidents.
By adopting these best practices, organizations can strengthen their defenses against supply chain attacks and better protect their critical assets and infrastructure. Frameworks like the NIST Cybersecurity Framework (CSF), which provides comprehensive guidelines and best practices for organizations to manage and reduce their cybersecurity risks (NIST, 2018), are suggested. In addition, the framework includes specific guidance for managing supply chain risks, such as incorporating supply chain risk management into overall risk management processes and conducting assessments of third-party providers.
Specific Best Practices for Critical Infrastructure:
To mitigate the risk of supply chain attacks, the energy sector can adopt several best practices, such as:
- Implement NERC CIP-013: NERC CIP-013 is a set of regulatory standards that require responsible entities to address supply chain risks for critical infrastructure in the energy sector (NERC, 2017). By implementing these standards, organizations can improve their supply chain risk management and enhance their overall cybersecurity posture.
- Share threat intelligence: Participate in industry-specific information-sharing groups and collaborate with peers to share threat intelligence, best practices, and lessons learned. This can help organizations stay informed about emerging threats and improve their ability to respond to supply chain attacks (DHS, n.d.).
The Role of Cyber Insurance in Managing Supply Chain Attacks
Cyber insurance can play a crucial role in managing the financial impact of supply chain attacks. A comprehensive cyber insurance policy can help organizations offset the costs associated with a breach, including incident response, legal fees, public relations efforts, and potential regulatory fines. Additionally, cyber insurance can cover business interruption costs and reimburse organizations for lost revenue due to downtime caused by a cyber attack.
To maximize the benefits of cyber insurance in the context of supply chain attacks, organizations should consider the following:
- Understand policy coverage: Evaluate the specific coverage offered by a cyber insurance policy, paying special attention to how it addresses supply chain attacks. Ensure that the policy covers damages arising from third-party vendor breaches, as these can be a significant source of risk in supply chain attacks.
- Evaluate policy limits and sub-limits: Assess the limits and sub-limits of your policy to ensure they are adequate for your organization's potential exposure. Supply chain attacks can have a wide-reaching impact, so it's essential to ensure that your coverage is sufficient to address potential losses.
- Align insurance coverage with risk management practices: Cyber insurance should be viewed as one component of a broader risk management strategy. Implement robust security measures and follow best practices for supply chain risk management to minimize the likelihood of a successful attack. This will not only reduce your risk exposure but may also lead to more favorable insurance premiums.
By incorporating cyber insurance into their overall risk management strategy, organizations can better manage the financial impact of supply chain attacks and enhance their overall cybersecurity posture.
What to Do If Your Organization with Industrial Control Systems and OT Networks Is a Victim of a Supply Chain Attack
If your organization with industrial control systems (ICS) and operational technology (OT) networks falls victim to a supply chain attack, it's crucial to respond effectively to minimize the impact. Start by activating your incident response plan, focusing on containing the breach and identifying its source. Isolate affected systems or network segments and disconnect any compromised third-party services.
As you work on containment, assess and remediate any vulnerabilities that may have contributed to the attack. Strengthen security measures by implementing network segmentation, enhancing access controls, and deploying advanced threat detection technologies specifically designed for ICS and OT networks. Engage external experts if necessary to assist with the investigation and recovery efforts, especially if your organization lacks the resources or expertise to handle a complex supply chain attack.
By focusing on these key recommendations, organizations with industrial control systems and operational technology networks can effectively respond to a supply chain attack, minimizing its impact on their critical assets and infrastructure.
Conclusion:
The X_Trader supply chain attack highlights the importance of addressing supply chain risks in critical infrastructure. By implementing robust security measures like NERC CIP-013 and NIST CSF and adopting best practices for supply chain risk management, organizations can enhance their overall cybersecurity posture and better protect themselves from the growing threat of supply chain attacks.
References:
- BleepingComputer. (2023). Critical infrastructure also hit by supply chain attack behind 3CX breach. Retrieved from https://www.bleepingcomputer.com/news/security/critical-infrastructure-also-hit-by-supply-chain-attack-behind-3cx-breach/
- CyberScoop. (2023). Modified X_Trader software led to compromise of two critical infrastructure targets. Retrieved from https://cyberscoop.com/3cx-x_trader-supply-chain-north-korea/
- DHS. (n.d.). Information Sharing and Analysis Centers (ISACs). Retrieved from https://www.cisa.gov/national-infrastructure-protection-plan/partnership-model/information-sharing-and-analysis-centers-isacs/
- NERC. (2017). CIP-013-1 - Cyber Security - Supply Chain Risk Management. Retrieved from https://www.nerc.com/pa/Stand/Reliability Standards/CIP-013-1.pdf
- NIST. (2018). Framework for Improving Critical Infrastructure Cybersecurity. Retrieved from https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf
- Gartner, "How to Respond to a Supply Chain Attack," (2021) https://www.gartner.com/smarterwithgartner/how-to-respond-to-a-supply-chain-attack
- Security Intelligence, "Supply Chain Attack: What It Is (and What to Do About It)," (2021) https://securityintelligence.com/articles/supply-chain-attack-what-it-is-what-to-do/
- Ponemon Institute. (2021). Cost of a Data Breach Report 2021. Retrieved from https://www.ibm.com/security/data-breach





