Behind the Screen: How W3LL's Phishing Kit Targets 50,000 Microsoft Accounts
The W3LL phishing syndicate has just targeted thousands of Microsoft business email accounts.
Established in 2017, a phishing syndicate recently came under the spotlight for targeting over 50,000 Microsoft business email accounts. They have employed a malicious tool capable of affecting one of the world's largest business email providers. This syndicate's phishing kit stands out as the most lucrative product in its market. With a clientele of over 500 users, these applications offer sophisticated and dynamic control over phishing campaigns. Their primary phishing kit provides the ability to execute a full Business Email Compromise (BEC) infection chain. There are currently more than 850 unique phishing websites created by various threat actors worldwide.
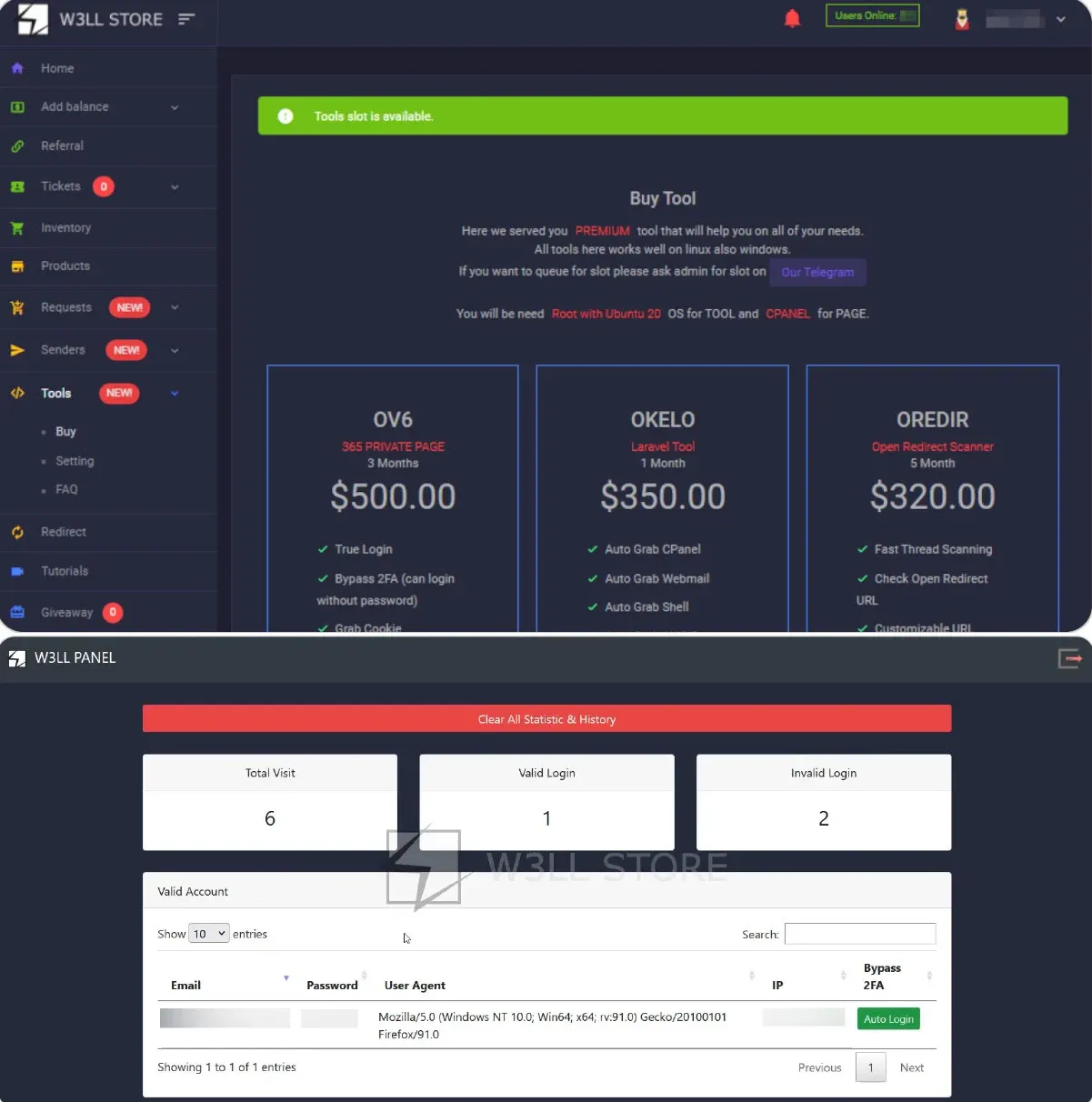
The products are available for purchase through an online underground store, where verified users can access and buy 16 customized tools. These tools include vulnerability scanners, link stagers, and SMTP senders. In the past 10 months, the syndicate has reportedly generated sales exceeding $500,000. These products cater to individuals with varying levels of IT expertise.
The primary targets of this phishing campaign are located in the US, UK, Australia, Germany, and Canada, with the most affected industries being IT, manufacturing, financial services, healthcare, and legal services. Most analytics and metrics are based on VirusTotal entries related to the attachments inserted into the phishing emails.
Phishing remains one of the cybercrime playbook's oldest and most enduring tactics. Its continued prevalence is due to its simplicity and effectiveness. Rather than launching prolonged server attacks, which can take days to succeed, malicious actors can achieve their goals by simply emailing their victims. Phishing, a form of social engineering, leverages the fact that the weakest link in an organization is often its users or employees, who are more susceptible to making errors than machines.
Infection Chain
In the case of the W3LL phishing kit, a threat actor can send a malicious email that, if successful, bypasses Multi-Factor Authentication (MFA). The BEC attack typically follows a sequence of stages: preparation, delivery of phishing emails, malicious link staging, account compromise, account discovery, and impact.
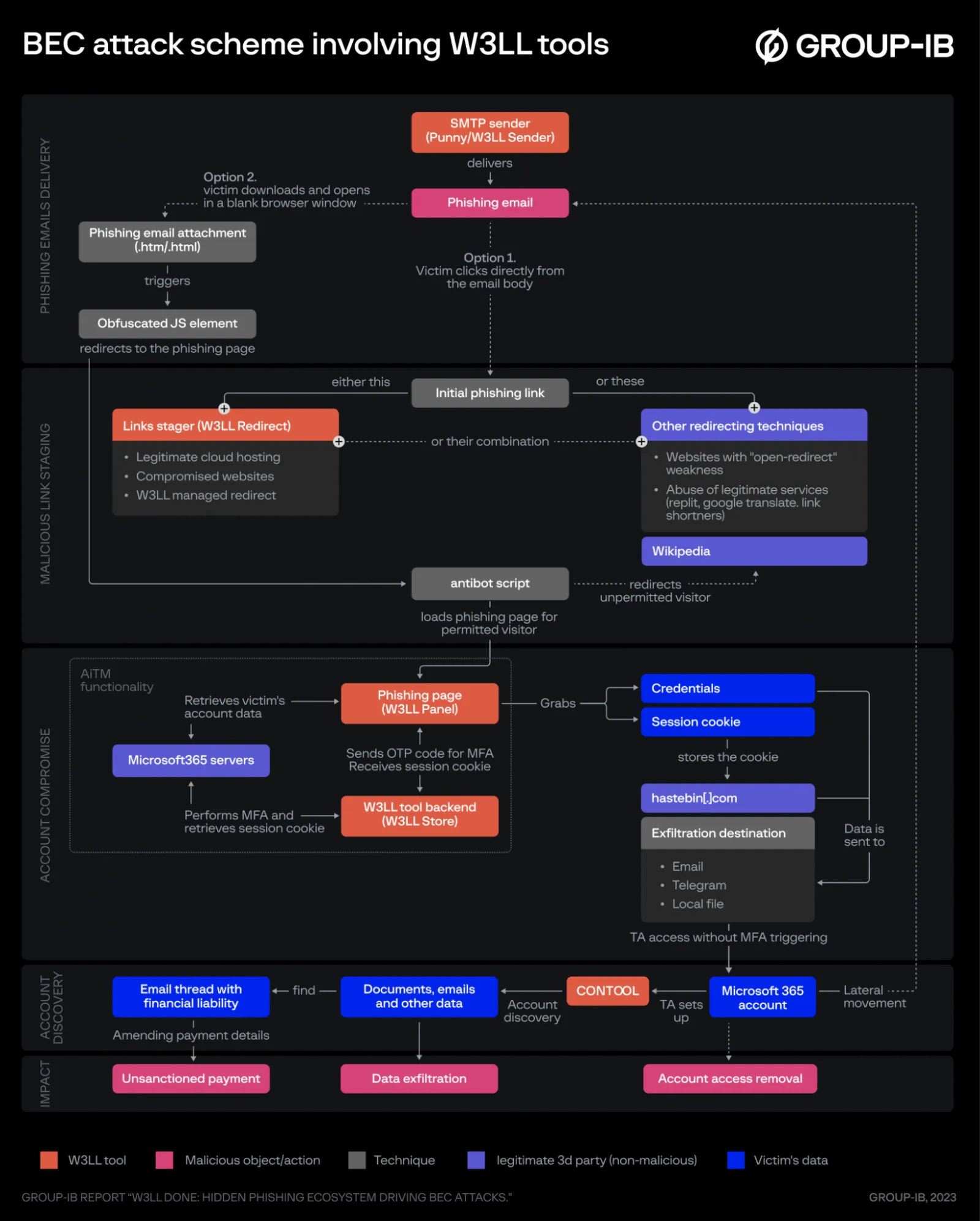
In the preparation phase, the attacker gathers as much information as possible about the target, including email addresses, birthdays, and possibly leaked usernames. They may also acquire other tools to complete the BEC toolkit.
Next, the attacker sends a phishing email designed to resemble a legitimate Microsoft notification, often with a sense of urgency (e.g., password reset). The attacker employs various obfuscation techniques to bypass spam filters and email analytics. The primary method for delivering the malicious payload is through an attachment disguised as a text or Word document but is, in reality, an HTML file.
When the user clicks on the link, they are directed to a legitimate landing page, which obscures the phishing page from security scrutiny. They encounter the malicious page only after navigating through a series of redirect URLs. The W3LL group hosts its own redirect tool known as "W3LL Redirect."
One of the final steps in the infection chain is Account Compromise. After clicking on the malicious email attachment, the user encounters a captcha in their browser. A fake login page then appears, prompting the victim to enter their email address. This email address is validated against a real Microsoft server for authentication. Using the validated email address, a brand identity fingerprint of the user's company is created via Microsoft's GetCredentialType feature. This fingerprint is used to mimic the branding of the victim's legitimate organization's login. Finally, the victim is asked for their password, which is sent to the attacker for exploitation.
If an organization has implemented MFA, the user is directed to a one-time pass (OTP) page, where they enter their OTP, expecting to gain access. The attacker now possesses the OTP and can sign in using the session cookie generated during this process.
Prevention
To prevent the success of such attacks, users are advised to employ FIDO v2.0 (physical MFA tools) or passwordless sign-in to mitigate OTP and session cookie theft. A zero-trust approach is recommended to strengthen access policies by utilizing trusted devices and IP allow/block list features. Organizations should monitor account activity, including logins, forwarding rules, deleted emails, and indicators of compromise (IOC). Employing an email security analysis tool between an organization's end-users and email servers is also crucial. Additionally, organizations should develop and practice policies and procedures for detecting, denying, and alerting against potential phishing campaigns.
Investigation
Investigations should be conducted promptly in the event of suspicious activity or a possible compromise within the organization. If a user or device is suspected of infection, it's advisable to disable internet connections on the affected device and deactivate the user's account. Passwords should be changed, authentication methods reviewed, and MFA tokens and backup codes reassigned after confirming contamination removal. Collecting as much data as possible before and after the IOC can help create a detailed infection chain of how the contamination succeeded.
Some indicators of compromise (IOCs) that may appear in logs or security queries include:
References
- 6, S. W3LL store: How a secret phishing syndicate targets 8,000+ microsoft 365 accounts. RedPacket Security. https://www.redpacketsecurity.com/w-ll-store-how-a-secret-phishing-syndicate-targets-microsoft-accounts/
- Ilascu, I. W3LL phishing kit hijacks thousands of Microsoft 365 accounts, bypasses MFA. BleepingComputer. https://www.bleepingcomputer.com/news/security/w3ll-phishing-kit-hijacks-thousands-of-microsoft-365-accounts-bypasses-mfa/
- Muncaster, P. Experts uncover underground phishing “empire"" w3ll. Infosecurity Magazine. https://www.infosecurity-magazine.com/news/experts-uncover-underground/
- Ushakov, A., & Berk, M. van den. (n.d.). W3LL DONE: HIDDEN PHISHING ECOSYSTEM DRIVING BEC ATTACK. https://www.group-ib.com/resources/research-hub/pdf






