Part 1: The Cyber Security Threat Landscape for Critical Infrastructure
October is #CybersecurityAwarenessMonth! Dive into the latest threats to critical infrastructure, from ransomware to supply chain risks.

In line with our unwavering commitment to the utility sector, we are delighted to introduce a comprehensive three-part series during the month of October, coinciding with Cybersecurity Awareness Month.
The first part in the series is meant to shed light on the pressing issue of cyber security threat landscape and key risks for critical infrastructure operators, specifically electric, water, and gas utilities. The next segment of the series will dive into technical aspects of cyber-attacks on critical infrastructure, and finally, the series will culminate with guidance on how to build an effective cyber security program.
The Increasingly Threatening Cyber Threat Landscape for Critical Infrastructure Operators
Let’s get into the complex realm of the cybersecurity threat landscape as it pertains to operators of critical infrastructure. The utilities sector, encompassing electric, water, and gas services, presents a particularly daunting challenge due to its vast and interconnected nature. The widespread distribution of operations and interdependencies with municipal departments significantly expands the potential attack surface. Not to mention that utilities/municipalities have the ability to pay ransomware. This, coupled with inherent vulnerabilities, has made utilities and municipalities prime targets for malicious actors.

As a result of the increasingly threatening cyber threat landscape, utility Executive Teams and Board of Directors are increasing the priority of cyber security within their organizations.
Ransomware – A Prevalent Threat
Based on lucrative payouts, there has been an increasing prevalence of ransomware attacks. Threat actors, ranging from organized criminal enterprises to nation-states, have honed their techniques to perfection. These attacks not only disrupt operations but also hold organizations hostage for hefty ransoms. Without robust protective measures in place, the consequences can be financially crippling and severely tarnish an organization's reputation.
Moreover, threat actors have evolved in their tactics. They now frequently breach trusted third parties to gain access to an ultimate target's environment, exploiting any vulnerabilities they discover along the way. This method not only underscores the importance of securing one's internal systems but also highlights the significance of bolstering the cybersecurity defenses of partners and suppliers.

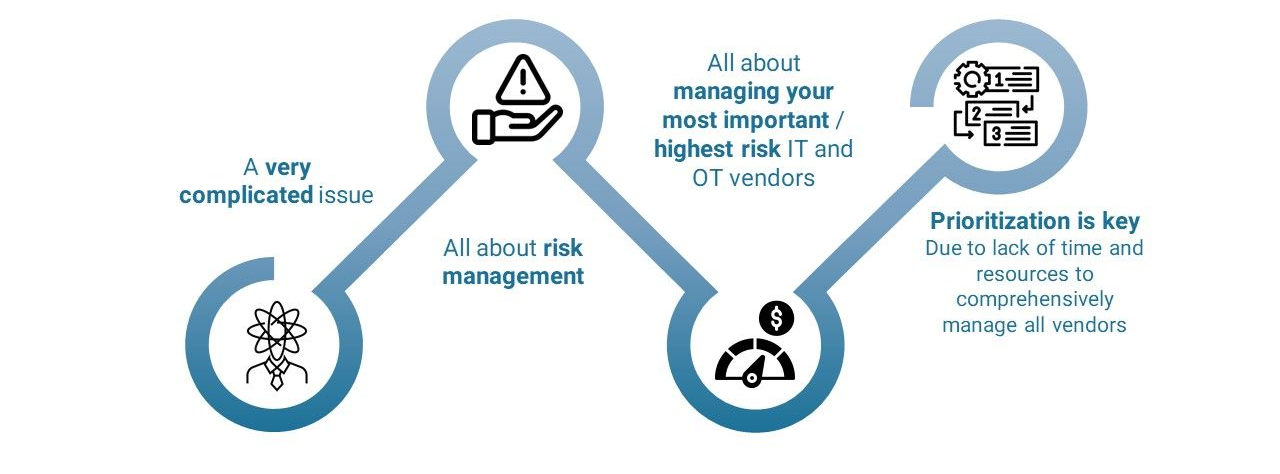
Supply Chain / Third Parties
Another pressing concern is the cybersecurity risks posed by supply chains, for example, your third-party vendors. Critical infrastructure entities heavily rely on external partners for products, entities are particularly susceptible to third party risks given the large dependence for products, services, maintenance, and support.
Managing vendors for cyber security risks can be summarized as follows:
Operational Technology
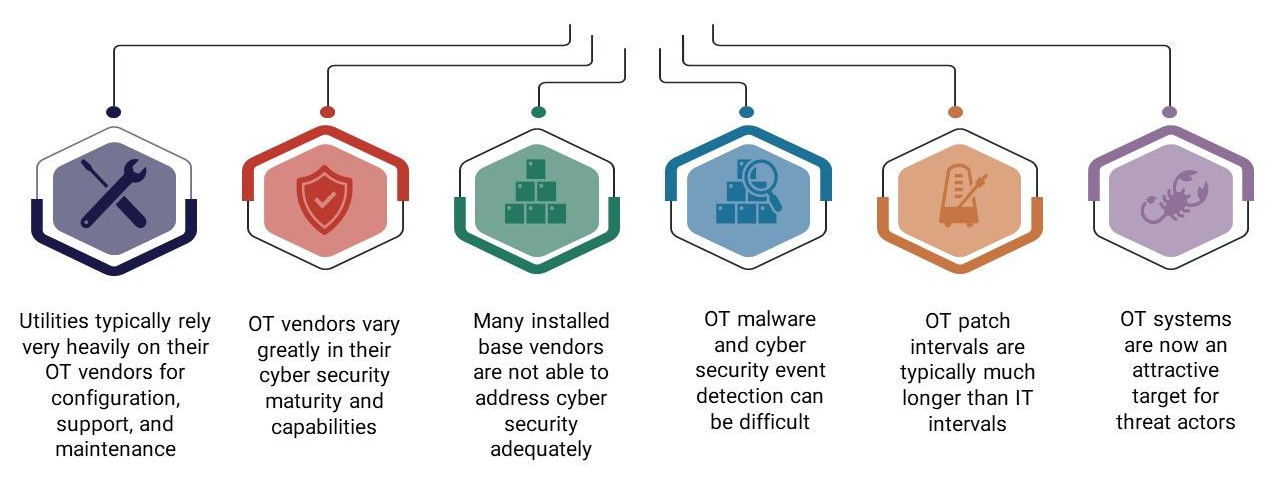
Operational Technology environments have evolved into alluring targets for threat actors. In addition to the conventional IT security risks faced by all sectors, critical infrastructure entities contend with unique cyber risks specific to their OT environments.
Summary
In summary, the cybersecurity threat landscape presents substantial risks to critical infrastructure entities. Regardless of their size, organizations must prioritize the implementation of a robust cybersecurity risk management program. As we navigate the digital age, our commitment remains—to equip you with the knowledge and tools needed to protect the vital infrastructure of your organization.
Stay tuned for the upcoming segment of our series, which will be released mid-October, that will describe the technical aspects of the more common breaches.
As an Industry Trusted Advisor - Acumen can assist you.
For more information, connect with an AESI risk management and governance specialist!





