Protect the Plug: Navigating Cyber Security Challenges for Managed EV Charging
Explore the intersection of EV technology and cyber threats, and understand key considerations for utilities, best practices, and the NIST Cybersecurity Framework for EV Charging. Discover how to foster a secure and sustainable future for EV adoption and energy systems with efficient programs.

A few months back, we wrote a post on how Managed Electric Vehicle (EV) Charging is a great load flexibility solution for utilities to consider. A critical component for utilities planning to implement this solution, though, is the cybersecurity of the managed EV charging infrastructure.
In case you missed the previous post, take a read!

In this post, during Cybersecurity Awareness Month, we'll explore the significance of cybersecurity for managed EV charging implementation and how electrical distribution utilities can protect their networks and customers.
Managed EV Charging - A Recap
As mentioned in our previous post, Managed EV charging is a dynamic and intelligent approach to charging that empowers utilities to optimize the distribution grid while providing EV owners with cost-effective and reliable charging services. While the risk of a cybersecurity incident may be minimal to non-existent in a passive management scheme (e.g., Time-of-Use pricing), in an active management scheme, where the utility is looking for more direct load control through either charging devices, electrical circuits or vehicle telematics, the cyber threat landscape become a lot larger. Increased connectivity and data sharing can make these systems vulnerable to cyber-attacks.
The Importance of Cybersecurity in a Managed EV Charging Landscape
The intersection of electric vehicle (EV) charging infrastructure and cybersecurity presents unique challenges and opportunities for distribution utilities. As utilities endeavor to implement managed EV charging programs, they must navigate a complex cybersecurity landscape to ensure their systems and data's integrity, availability, and confidentiality. The primary cybersecurity considerations include:
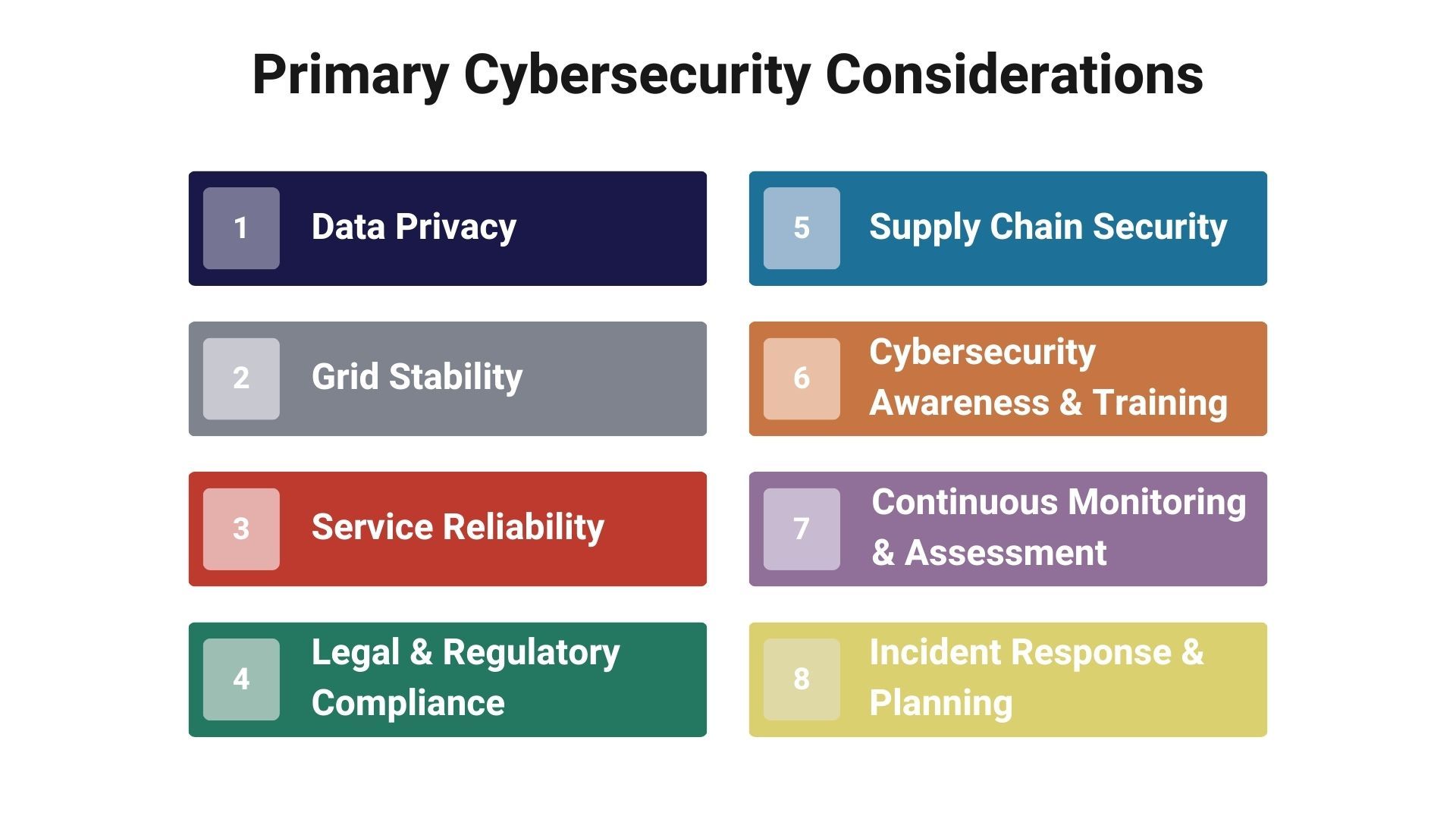
Data Privacy
EV charging networks accumulate significant data, encompassing charging locations, usage patterns, and payment information. Protecting this data is paramount to uphold the privacy rights of EV owners and sustain customer trust. Implementing robust encryption standards, access control measures, and data anonymization techniques can mitigate the risk of data breaches and unauthorized access.
Grid Stability
One of the major advantages of managed EV charging is the capability to modulate the EV load in alignment with grid loading requisites, thus enhancing grid stability. However, a cybersecurity incident, such as a denial-of-service attack, could impede the utility's ability to manage EV charging, potentially leading to power outages and system failures. Thus, cybersecurity measures are instrumental in safeguarding grid stability.
Service Reliability
With a customer-centric approach, the managed EV charging experience must be reliable and seamless for the end user. Cyber-attacks could result in the unavailability of charging infrastructure or mismanagement of the EV charging experience, discouraging customer participation and possibly deterring further EV adoption. Implementing resilience measures, such as redundancy and failover capabilities, can enhance service reliability even in the face of cyber threats.
Legal and Regulatory Compliance
Utilities are mandated to adhere to a range of data protection and cybersecurity regulations, including the General Data Protection Regulation (GDPR) and industry-specific standards like NIST frameworks. Compliance mitigates legal and financial risks and drives the adoption of cybersecurity best practices within the organization.
Supply Chain Security
The security of the supply chain is pivotal as vulnerabilities can be introduced through hardware, software, or services procured from third-party vendors. Ensuring that suppliers adhere to stringent cybersecurity standards and conducting regular security assessments can mitigate supply chain risks.
Cyber Security Awareness and Training
Fostering a culture of cybersecurity awareness among utility staff and end-users is crucial. Regular training and awareness campaigns can significantly reduce the likelihood of successful phishing attacks and other user-centric threats.
Continuous Monitoring and Assessment
The cybersecurity landscape is dynamic with evolving threat vectors. Continuous monitoring of the managed EV charging infrastructure, regular security assessments, and adopting a proactive cybersecurity stance are essential for promptly identifying and mitigating potential threats.
Incident Response and Recovery
Having a well-defined incident response plan and recovery strategies to critical to mitigate the impact of cybersecurity incidents when they occur. These plans should be regularly tested and updated to align with the changing cybersecurity landscape.
By comprehensively addressing these cybersecurity considerations, utilities can create a robust foundation for successfully implementing and operating managed EV charging programs. This holistic approach to cybersecurity will significantly promote the sustainable growth of EV charging infrastructure, thereby contributing to the broader goals of grid modernization and the transition to cleaner, more resilient energy systems.
Securing Managed EV Charging Infrastructure
Adopting cybersecurity best practices is paramount for electrical utilities venturing into managed EV charging programs. Integrating Electric Vehicle (EV) charging infrastructure with existing utility systems exposes a new realm of cybersecurity vulnerabilities. The following methods, aligned with the NIST Cybersecurity Framework for EV Charging (NIST IR 8473), are instrumental in bolstering the cybersecurity posture of a managed EV charging program:
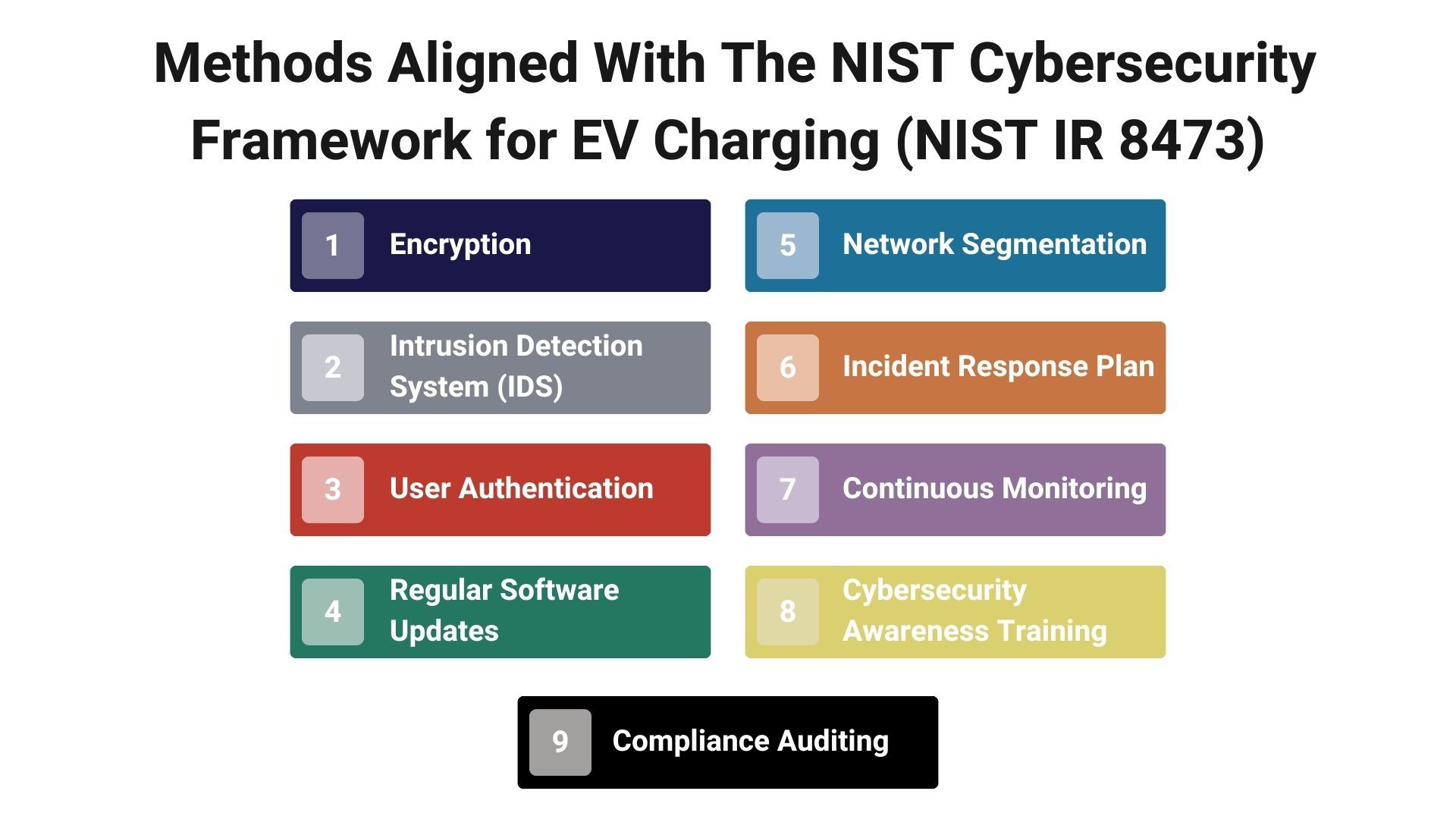
Encryption
Implementing robust encryption protocols is crucial for ensuring the confidentiality and integrity of data in transit between charging stations, users, and the utility's backend systems. Adherence to encryption standards such as AES 256-bit encryption can significantly mitigate the risk of data interception and unauthorized access.
Intrusion Detection Systems (IDS)
Employing IDS technologies enables real-time monitoring and detection of suspicious activities or potential cyber threats within the managed charging network. This aligns with the NIST CSF's Detect Function, which emphasizes the importance of continuous monitoring and anomaly detection.
User Authentication
Strong authentication methods, including multi-factor authentication (MFA), are vital to ensure that only authorized users can access and utilize the charging infrastructure. This measure resonates with the Access Control (PR.AC) Category of the NIST CSF, underscoring the significance of limiting access to authorized individuals.
Regular Software Updates
Ensuring the software and firmware of charging stations are up to date is crucial to patching known vulnerabilities and protecting against evolving threats. As delineated in the NIST CSF, adherence to a systematic Patch Management process is pivotal in maintaining a secure operational environment.
Network Segmentation
Isolating sensitive components of the grid and charging network through network segmentation restricts lateral movement of potential adversaries in the network, thereby limiting the impact of a breach. This measure aligns with the NIST CSF's guidance on created segmented networks to protect critical infrastructure.
Incident Response Plan
Developing a comprehensive incident response plan, as the NIST CSF's Respond Function advocates, is critical to ensure swift mitigation and recovery from cyber incidents. This plan should encompass defined roles, communication protocols, and recovery procedures to restore operations swiftly.
Continuous Monitoring
It is implementing a continuous monitoring strategy to scrutinize the security posture of the EV charging infrastructure continuously. This aligns with the Monitoring (DE.CM) Category of the NIST CSF, which emphasizes the importance of detecting and responding to cybersecurity events in a timely manner.
Cyber Security Awareness Training
Conducting regular cybersecurity awareness training for utility staff and stakeholders involved in the managed EV charging program. This initiative, in line with the NIST CSF's Awareness and Training (PR.AT) Category, aims to foster a culture of cybersecurity vigilance.
Compliance Auditing
Conducting regular audits to ensure compliance with applicable legal, regulatory, and industry-specific cybersecurity standards. This proactive approach facilitates the early identification of compliance gaps and fosters a culture of continuous improvement in cybersecurity practices.
Employing a holistic approach to cybersecurity, encapsulating the above measures and aligning with the guidelines provided in the NIST Cybersecurity Framework for EV Charging will significantly contribute to the secure and resilient operation of managed EV charging infrastructure. This comprehensive cybersecurity strategy mitigates risks and instills trust among EV owners and other stakeholders, fostering a conducive environment for the widespread adoption of managed EV charging programs.
The NIST Cybersecurity Framework for EV Charging
The National Institute of Standards and Technology (NIST) provides a robust framework for improving critical infrastructure cybersecurity, including the landscape of Electric Vehicle (EV) Charging. The recently released NIST Interagency Report (NIST IR 8473) presents a Cybersecurity Framework Profile for Electric Vehicle Extreme Fast Charging Infrastructure, which can also be adapted for managed EV charging scenarios.
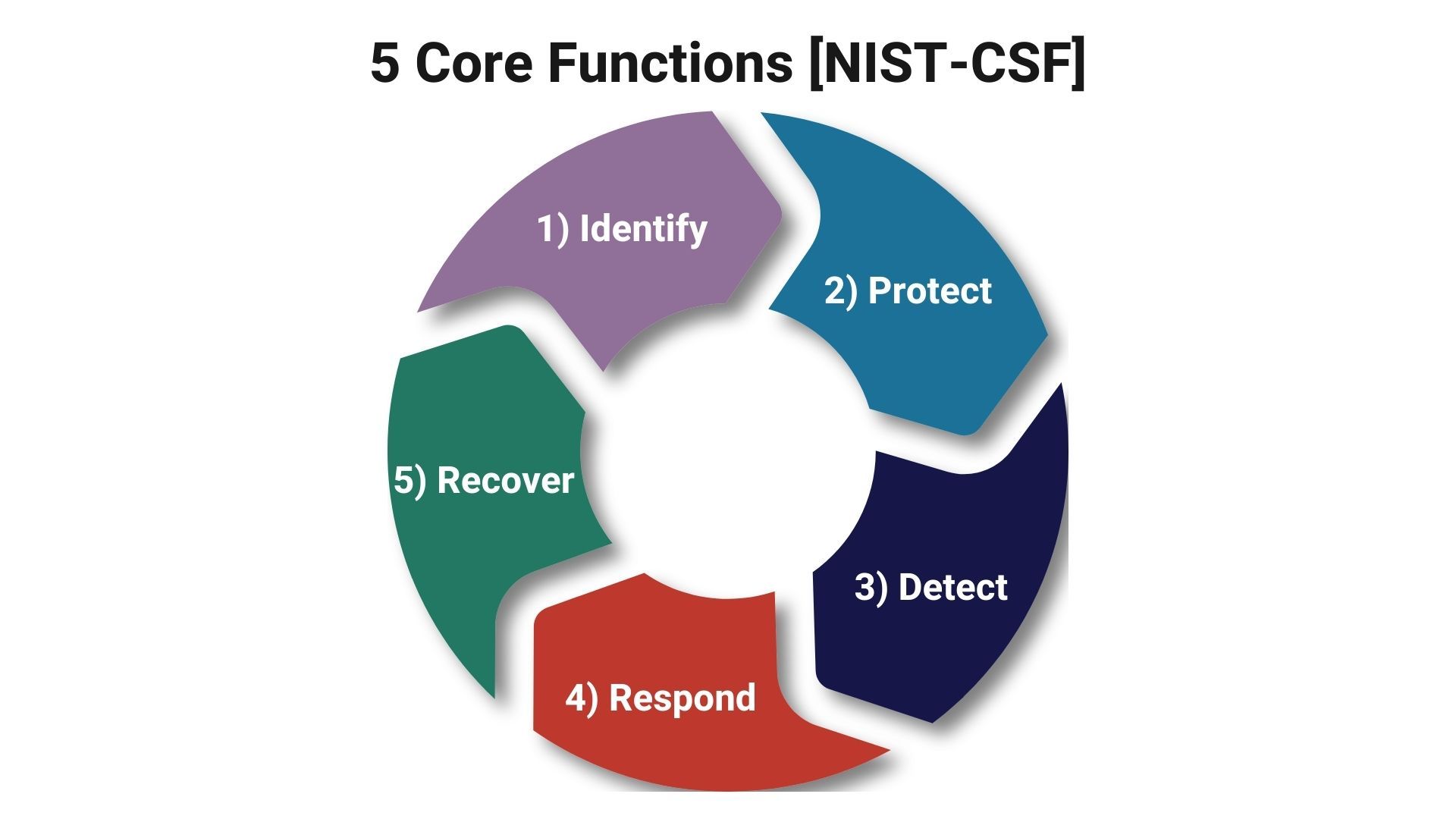
Identify
At the outset, it's imperative to identify and understand the cyber ecosystem surrounding the managed EV charging infrastructure. This involves recognizing the data flows, system interfaces, and the stakeholders involved - from EV owners to grid operators and service providers.
Protect
Adopt protective measures to ensure data and services' confidentiality, integrity, and availability. This includes encrypting sensitive data, employing strong user authentication mechanisms, and ensuring the physical security of the charging infrastructure.
Detect
Utilize advanced detection systems like Intrusion Detection Systems (IDS) and other monitoring tools to identify anomalies and potential cyber threats swiftly. Continuous monitoring and real-time alerts are crucial for early detection of cyber incidents.
Respond
Develop and maintain a robust incident response plan to address any cyber security incidents that may occur. This involves defining protocols for communicating, investigating, and mitigating incidents, ensuring swift recovery and minimizing adverse impacts.
Recover
Post-incident, it's crucial to analyze the events, learn from them, and update the recovery plans accordingly. Incorporating lessons learned into recovery strategies will enhance the resilience of the managed EV charging infrastructure against future threats.
In addition to the above, adherence to regulatory and compliance standards like GDPR and industry-specific standards is paramount in ensuring a robust cybersecurity posture. Utilities can also consider engaging with cybersecurity consultants specializing in the energy sector to tailor the NIST guidelines to their specific operational environment.
Furthermore, collaboration with other stakeholders in the EV ecosystem, including manufacturers, service providers, and regulatory bodies, can foster a culture of cybersecurity awareness and shared responsibility. This collaborative approach enhances the cybersecurity of managed EV charging and fosters trust amongst consumers and stakeholders, accelerating EV adoption and the transition towards a more sustainable and resilient energy infrastructure.
Training and Communication
A cornerstone of any good cybersecurity program is ensuring that the appropriate subject matter experts are engaged, the appropriate utility staff is adequately trained, and, in the case of a customer-facing application such as managed EV charging, there is open and transparent communication with the end user. Therefore, it is imperative that cybersecurity not be an afterthought but be included in every step - planning, design, and implementation of a managed EV charging program.

In conclusion, we would like to say that as managed EV charging becomes a vital component of the utility and EV ecosystem, its security is paramount for distribution utilities and EV owners. As EV adoption continues to grow, the focus on cybersecurity must remain strong to ensure data privacy, grid stability, service reliability and regulatory compliance. By implementing robust security measures from the early stages of planning such a program and staying informed about evolving threats, utilities can effectively manage the cybersecurity of their charging infrastructure and support the sustainable future of mobility.
This is a key differentiator at Acumen, where we can help you plan, design and implement a grid flexibility program, such as managed EV charging while ensuring a comprehensive cybersecurity program is embedded from the beginning.
Connect with an Acumen expert to learn more!







