Part 2: Understanding the Technical Twists of Threats and Incidents
Explore the technical underpinnings of today's cyber threats, from the inner workings of ransomware to the hidden vulnerabilities in third-party relationships. Dive into real-world incidents and gain insights to fortify your digital defenses.

In our previous post, we began exploring the cyber threat landscape facing critical infrastructure sectors. Now, as we step further into Cybersecurity Awareness Month, let's delve a bit deeper into what makes these threats tick on a technical level. Through the lens of real-world incidents and a touch of expertise, we aim to shed light on how bad actors take advantage of weak spots in both IT and OT environments, focusing especially on ransomware and third-party risks.
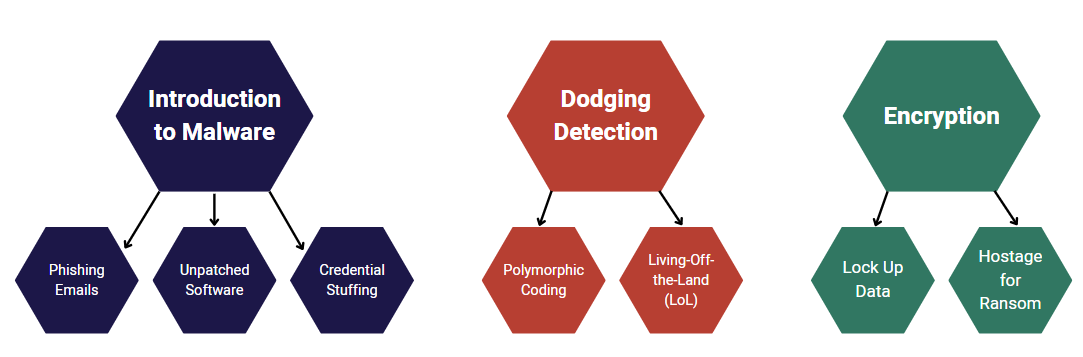
Ransomware - What's Under the Hood?
Ransomware doesn't just appear out of thin air; it's the end result of carefully exploited weaknesses. Here's how it generally plays out:
- The usual suspects include phishing emails, unpatched software, and credential stuffing
- Today's ransomware has gotten pretty good at dodging detection with tricks like polymorphic coding and living-off-the-land (LoL) tehniques
- Once inside, ransomware uses strong encryption to lock up data, holding it hostage for a ransom
Real-World Incident
In a notable incident, a critical infrastructure organization in the US fell victim to a ransomware attack orchestrated by the Cuba ransomware group. The group launched a complex attack by exploiting a couple of known vulnerabilities. Firstly, a vulnerability in Veeam Backup & Replication software (CVE-2023-27532) was exploited, potentially allowing attackers to access credentials stores on victim's devices through the Veeam backup service running on a specific network port (TCP port 9401). Secondly, Microsoft's NetLogon protocol had a flaw (CVE-2020-1472, known as "ZeroLogon") that could let attackers to escalate privileges to obtain admin access on active directory domain controllers.

Third-Party and Supply Chain Risks - The Hidden Links
Our organizations are often closely tied with third-party vendors. The technical interactions in these relationships can sometimes open doors to risks:
- Strong access control for vendors accessing your network is key
- keeping third-party access limited to certain areas of the network can help prevent bad actors from wandering around your network
The SolarWinds incident showed us how bad actors can sneak in through third-party software and cause a lot of damage, highlighting the need to really vet the security practices of our vendors.
Operational Technology (OT) - A New Playing Field
Bad actors are getting creative, and OT environments are now in the spotlight.
- Many OT protocols weren't built with security in mind, making them easy targets
- Old, outdated systems can be a goldmine for bad actors
Real World Incident
In 2015, a Ukranian power grid was attacked, showing us the harsh reality of what happens when OT environments are compromised. Weak security protocols within the OT network were exploited, stressing the need for up-to-date security measures in these areas.
Summary
Peeling back the technical layers of cyber threats helps us better prepare and defend our critical infrastructure. Stay tuned for the final piece in this series, where we'll walk through building a solid cybersecurity program to weather these stormy cyber seas.
Did you miss the first part to the series? Read it here!

As an Industry Trusted Advisor - Acumen can assist you.
For more information, connect with an AESI risk management and governance specialist!







