Part 3: How to Build an Effective Cyber Security Program
Learn how to integrate a robust cybersecurity program into your Enterprise Risk Management, engage a cross-functional team, adopt industry standards, and safeguard against third-party threats. Don't leave your critical infrastructure exposed.

In line with our unwavering commitment to the utility sector, we are pleased to introduce a comprehensive three-part series during the month of October, coinciding with Cybersecurity Awareness Month.
The first part in the series provided context on the cybersecurity threat landscape and key risks for critical infrastructure operators, specifically electric, water, and gas utilities. The second in the series dove into technical aspects of cyber-attacks on critical infrastructure, and the series culminates with this blog on how to build an effective cybersecurity program.
Integrate Your Cyber Security Program into Your Overall Enterprise Risk Management Program
As has been stated throughout this series, cyber security is not an IT issue, but rather it is a risk management and governance issue that Executives and Boards need to tightly oversee, manage, and support. Cybersecurity risk management should not be a standalone initiative - it should be integrated into your overall Enterprise Risk Management (ERM) program.
Include cyber and physical security as an area of risk in your ERM, just as you would include other risk areas such as major weather events and labor relations. Use the same risk register that you use for all risks. Feeding the risk register can be cybersecurity program audits, third party vulnerabilities, assessments and penetration tests that you or a third party executes. Patching should be a continuous risk register action with priority, since delays in patching translates into vulnerable systems.
Engage a Cross-Functional Team
Your cyber program will fail if you do not engage a cross-functional team as shown in the following visual. Chose a leader for the program, someone with decision making skills and access to the Executive Team.
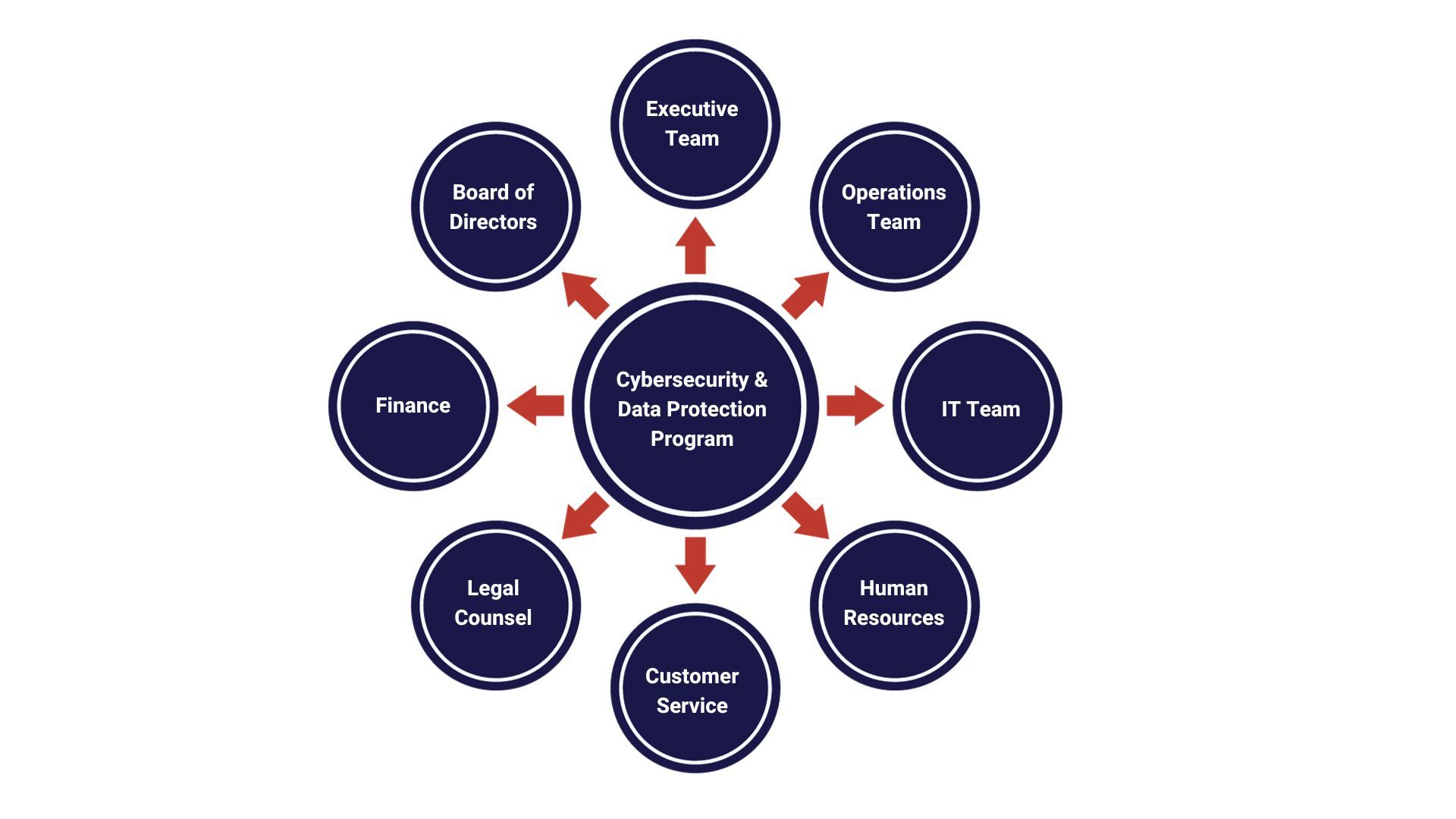
Adopt Standards, Ensure Balance Across the Three Legs of the Stool
Adopting standards for your cybersecurity program is essential to ensure longevity and industry support. The NIST Cybersecurity Framework is an ideal standard for electric, water, and gas utilities and it encompasses your organization holistically across enterprise (including an associated municipality), IT, and Operational Technology (OT) Functions.
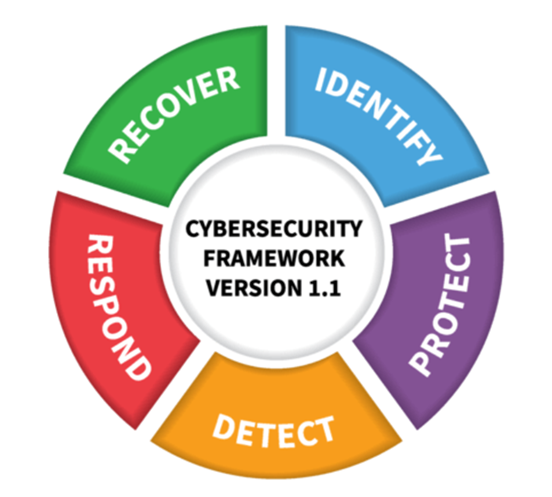
The NIST Framework includes controls from people, governance, & process, and technology controls. Ensure that your program is not solely focused on technology.
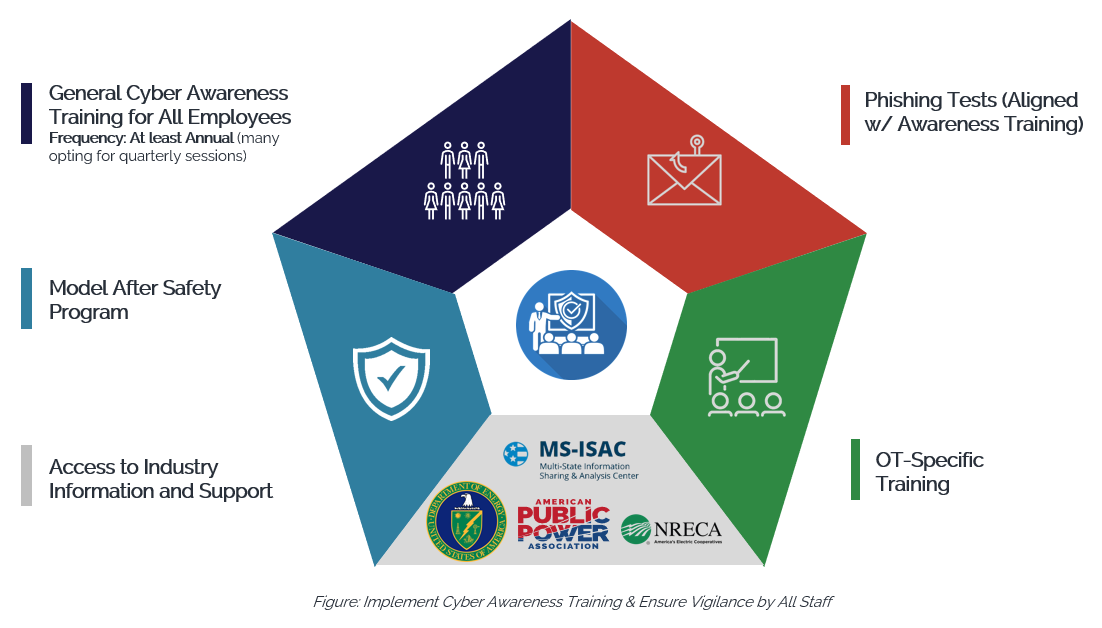
Implement Cyber Awareness Training and Ensure Vigilance by All Staff
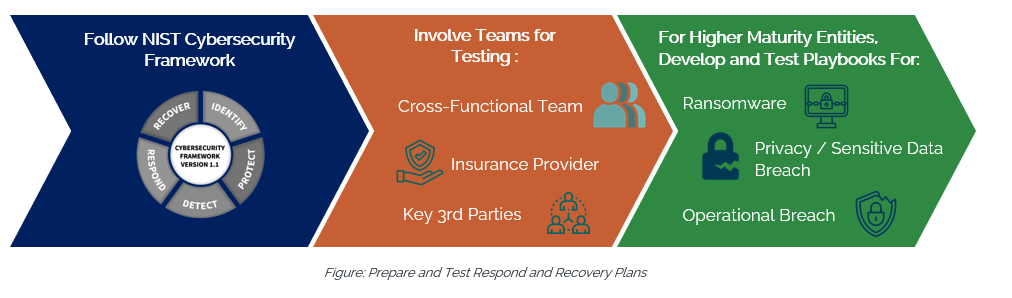
Prepare and Test Respond and Recovery Plans
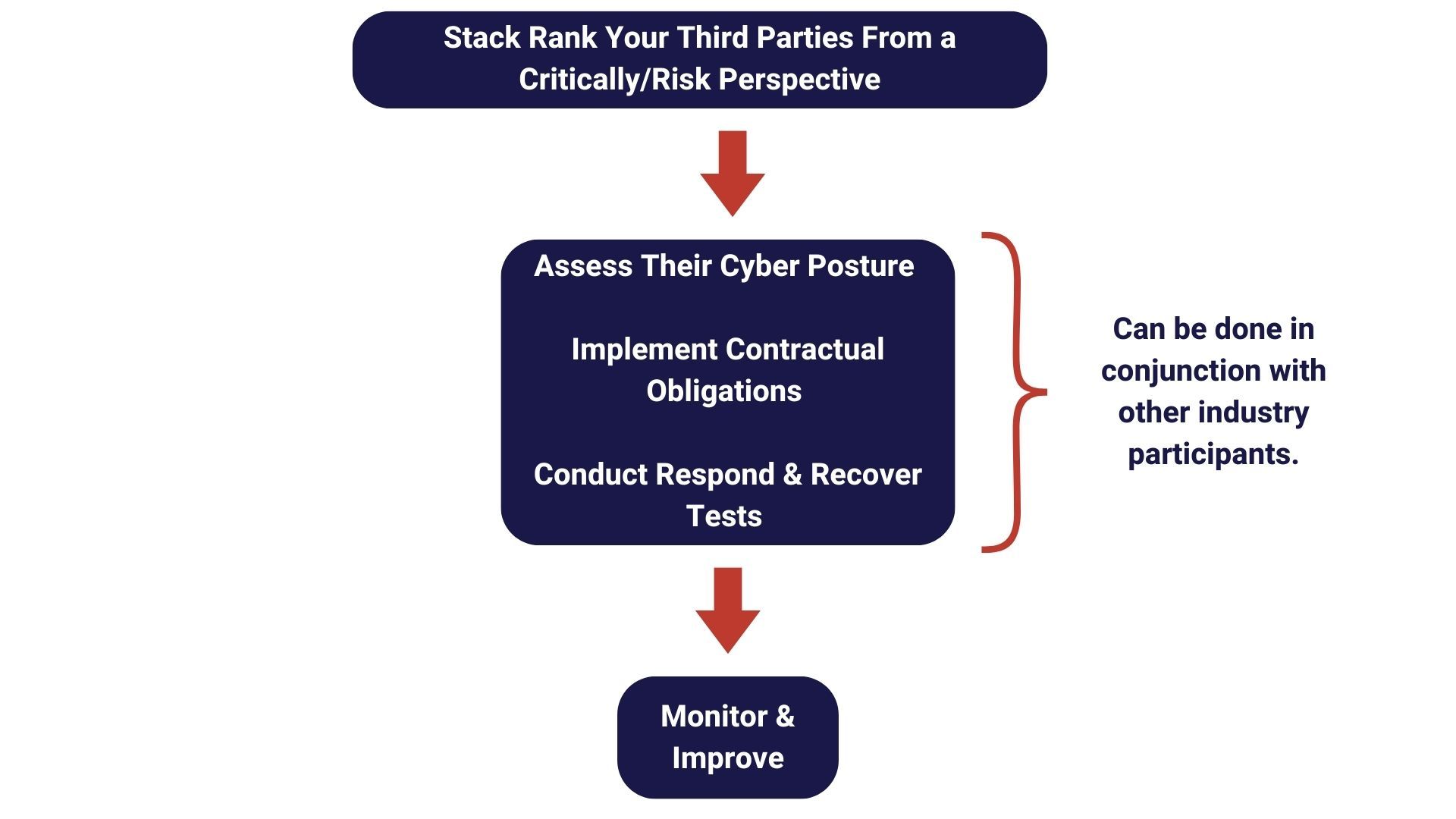
Manage Your Third Parties
As stated in the first in this series, your key third party vendors now represent a significant cybersecurity risk to critical infrastructure entities. Critical infrastructure entities are particularly susceptible to third party risks given the large dependence on vendors for products, services, maintenance, and support.
The following visual shows at a high level the elements of vendor cyber management:
Summary
The cyber threat landscape presents significant risks for critical infrastructure entities. All entities regardless of size need to implement an effective cyber security risk management program.
Did you miss the first two parts to this series? Read Part 1 and Part 2 here!


As an Industry Trusted Advisor - Acumen can assist you.
For more information, connect with an AESI risk management and governance specialist!






